Vol. 3C 24-11
VIRTUAL MACHINE CONTROL STRUCTURES
Table 24-7 lists the secondary processor-based VM-execution controls. See Chapter 25 for more details of how
these controls affect processor behavior in VMX non-root operation.
All other bits in this field are reserved to 0. Software should consult the VMX capability MSR
IA32_VMX_PROCBASED_CTLS2 (see Appendix A.3.3) to determine which bits may be set to 1. Failure to clear
reserved bits causes subsequent VM entries to fail (see Section 26.2.1.1).
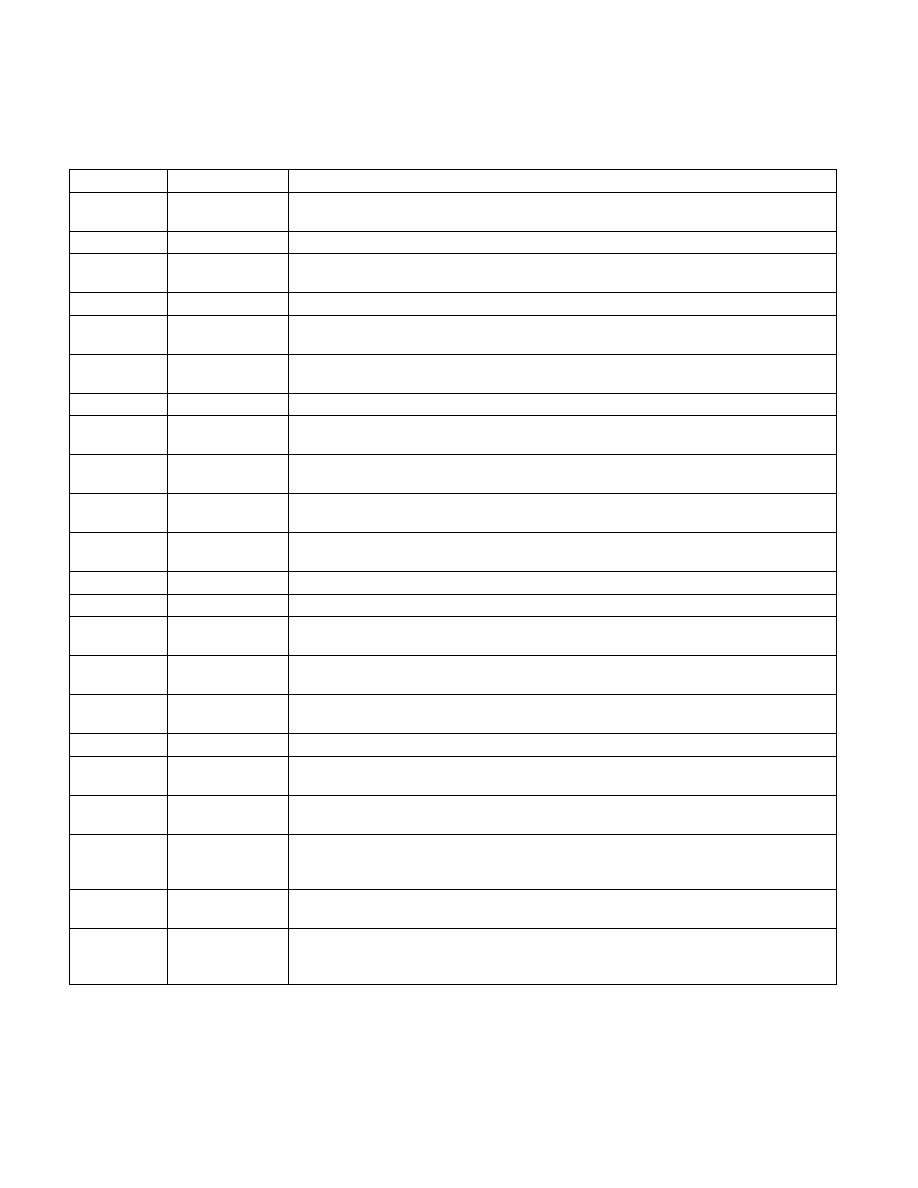
Table 24-7. Definitions of Secondary Processor-Based VM-Execution Controls
Bit Position(s) Name
Description
0
Virtualize APIC
accesses
If this control is 1, the logical processor treats specially accesses to the page with the APIC-
access address. See Section 29.4.
1
Enable EPT
If this control is 1, extended page tables (EPT) are enabled. See Section 28.2.
2
Descriptor-table
exiting
This control determines whether executions of LGDT, LIDT, LLDT, LTR, SGDT, SIDT, SLDT, and
STR cause VM exits.
3
Enable RDTSCP
If this control is 0, any execution of RDTSCP causes an invalid-opcode exception (#UD).
4
Virtualize x2APIC
mode
If this control is 1, the logical processor treats specially RDMSR and WRMSR to APIC MSRs (in
the range 800H–8FFH). See Section 29.5.
5
Enable VPID
If this control is 1, cached translations of linear addresses are associated with a virtual-
processor identifier (VPID). See Section 28.1.
6
WBINVD exiting
This control determines whether executions of WBINVD cause VM exits.
7
Unrestricted guest This control determines whether guest software may run in unpaged protected mode or in real-
address mode.
8
APIC-register
virtualization
If this control is 1, the logical processor virtualizes certain APIC accesses. See Section 29.4 and
9
Virtual-interrupt
delivery
This controls enables the evaluation and delivery of pending virtual interrupts as well as the
emulation of writes to the APIC registers that control interrupt prioritization.
10
PAUSE-loop exiting This control determines whether a series of executions of PAUSE can cause a VM exit (see
Section 24.6.13 and Section 25.1.3).
11
RDRAND exiting
This control determines whether executions of RDRAND cause VM exits.
12
Enable INVPCID
If this control is 0, any execution of INVPCID causes a #UD.
13
Enable
VM functions
Setting this control to 1 enables use of the VMFUNC instruction in VMX non-root operation. See
14
VMCS shadowing
If this control is 1, executions of VMREAD and VMWRITE in VMX non-root operation may access
a shadow VMCS (instead of causing VM exits). See Section 24.10 and Section 30.3.
15
Enable ENCLS
exiting
If this control is 1, executions of ENCLS consult the ENCLS-exiting bitmap to determine whether
the instruction causes a VM exit. See Section 24.6.16 and Section 25.1.3.
16
RDSEED exiting
This control determines whether executions of RDSEED cause VM exits.
17
Enable PML
If this control is 1, an access to a guest-physical address that sets an EPT dirty bit first adds an
entry to the page-modification log. See Section 28.2.5.
18
EPT-violation #VE
If this control is 1, EPT violations may cause virtualization exceptions (#VE) instead of VM exits.
19
Conceal VMX non-
root operation from
Intel PT
If this control is 1, Intel Processor Trace suppresses data packets that indicate the use of
virtualization (see Chapter 36).
20
Enable
XSAVES/XRSTORS
If this control is 0, any execution of XSAVES or XRSTORS causes a #UD.
25
Use TSC scaling
This control determines whether executions of RDTSC, executions of RDTSCP, and executions
of RDMSR that read from the IA32_TIME_STAMP_COUNTER MSR return a value modified by the
TSC multiplier field (see Section 24.6.5 and Section 25.3).