Vol. 3D 42-9
INTEL® SGX INTERACTIONS WITH IA32 AND INTEL® 64 ARCHITECTURE
executing EEXIT. However, successful execution of the ENCLU[EEXIT] leaf function restores XCR0 to the value it
held at the time of the most recent enclave entry.
42.7.8
Processor Extended States and ENCLU[EREPORT]
The ENCLU[EREPORT] leaf function creates the MAC-protected REPORT structure that reports on the enclaveÔÇÖs
identity. ENCLU[EREPORT] includes in the report the values of SECS.ATTRIBUTES.XFRM and SECS.MISCSELECT.
42.7.9 Processor
Extended
States and ENCLU[EGETKEY]
The ENCLU[EGETKEY] leaf function returns a cryptographic key based on the information provided by the KEYRE-
QUEST structure. Intel SGX provides the means for isolation between different operating conditions by allowing an
enclave developer to select which bits out of XFRM and MISCSELECT need to be included in the derivation of the
keys.
42.8 INTERACTIONS
WITH
SMM
42.8.1
Availability of Intel® SGX instructions in SMM
Enclave instructions are not available in SMM, and any attempt to execute ENCLS or ENCLU instructions inside SMM
results in an invalid-opcode exception (#UD).
42.8.2
SMI while Inside an Enclave
If the logical processor executing inside an enclave receives an SMI, the logical processor exits the enclave asyn-
chronously. The response to an SMI received while executing inside an enclave depends on whether the dual-
monitor treatment is enabled. For detailed discussion of transfer to SMM, see Chapter 34, ÔÇťSystem Management
ModeÔÇŁ of the Intel┬« 64 and IA-32 Architectures Software DeveloperÔÇÖs Manual, Volume 3C.
If the logical processor executing inside an enclave receives an SMI when dual-monitor treatment is not enabled,
the logical processor exits the enclave asynchronously, and transfers the control to the SMM handler. In addition to
saving the synthetic architectural state to the SMRAM State Save Map (SSM), the logical processor also sets the
ÔÇťEnclave InterruptionÔÇŁ bit in the SMRAM SSM (bit position 1 in SMRAM field at offset 7EE0H).
If the logical processor executing inside an enclave receives an SMI when dual-monitor treatment is enabled, the
logical processor exits the enclave asynchronously, and transfers the control to the SMM monitor via SMM VM exit.
The SMM VM exit sets the ÔÇťEnclave InterruptionÔÇŁ bit in the Exit Reason (see Table 42-1) and in the Guest Interrupt-
ibility State field (see Table 42-2) of the SMM VMCS.
42.8.3
SMRAM Synthetic State of AEX Triggered by SMI
All processor registers saved in the SMRAM have the same synthetic values listed in Section 40.3. Additional
SMRAM fields that are treated specially on SMI are:
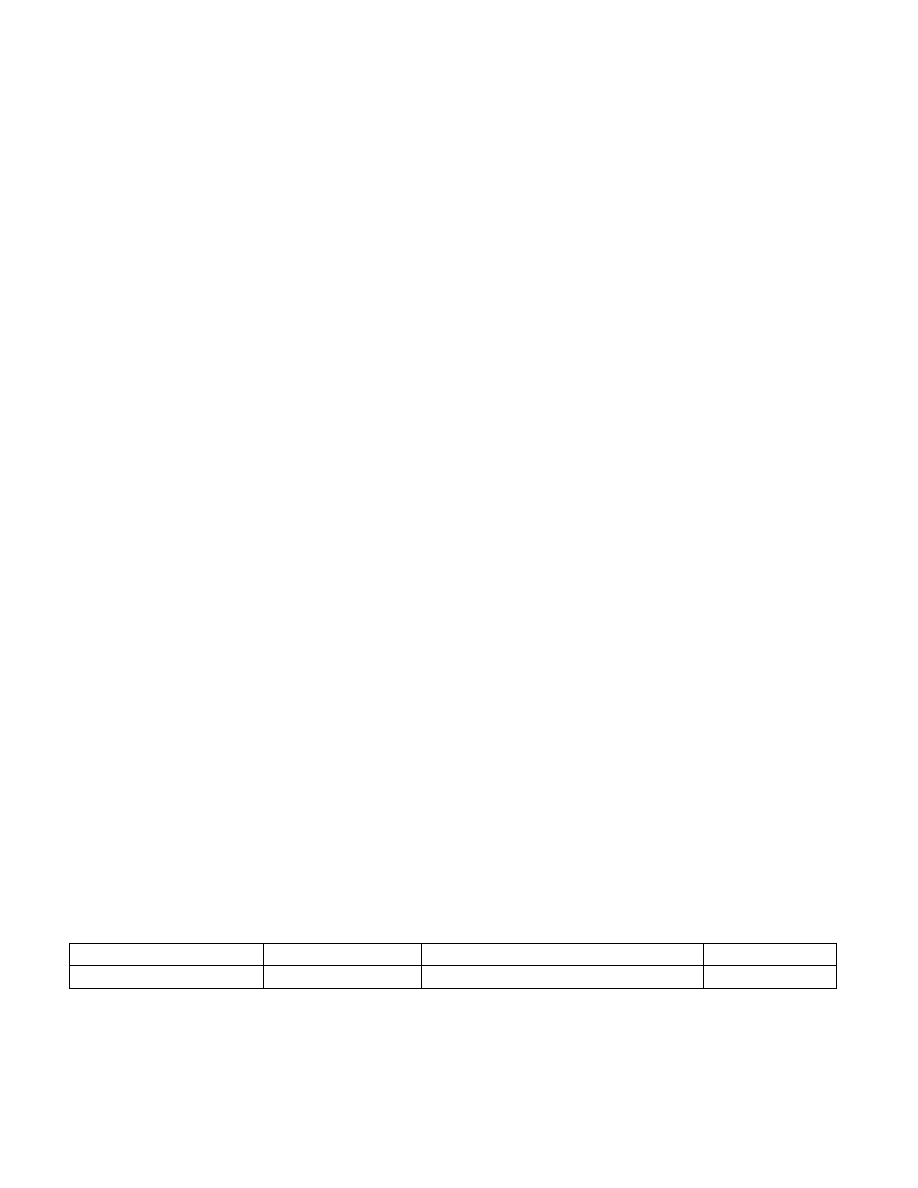
Table 42-1. SMRAM Synthetic States on Asynchronous Enclave Exit
Position
Field
Value
Writable
SMRAM Offset 07EE0H.Bit 1
ENCLAVE_INTERRUPTION Set to 1 if exit occurred in enclave mode
No