Vol. 3D 42-11
INTEL® SGX INTERACTIONS WITH IA32 AND INTEL® 64 ARCHITECTURE
42.11.3 Interactions with Authenticated Code Modules (ACMs)
Intel SGX only allows launching ACMs with an Intel SGX SVN that is at the same level or higher than the expected
Intel SGX SVN. The expected Intel SGX SVN is specified by BIOS and locked down by the processor on the first
successful execution of an Intel SGX instruction that doesn’t return an error code. Intel SGX provides interfaces for
system software to discover whether a non faulting Intel SGX instruction has been executed, and evaluate the suit-
ability of the Intel SGX SVN value of any ACM that is expected to be launched by the OS or the VMM.
These interfaces are provided through a read-only MSR called the IA32_SGX_SVN_STATUS MSR (MSR address
500h). The IA32_SGX_SVN_STATUS MSR has the format shown in Table 42-2.
OS/VMM that wishes to launch an architectural ACM such as SINIT is expected to read the IA32_SGX_SVN_STATUS
MSR to determine whether the ACM can be launched or a new ACM is needed:
•
If either the Intel SGX SVN of the ACM is greater than the value reported by IA32_SGX_SVN_STATUS, or the
lock bit in the IA32_SGX_SVN_STATUS is not set, then the OS/VMM can safely launch the ACM.
•
If the Intel SGX SVN value reported in the corresponding component of the IA32_SGX_SVN_STATUS is greater
than the Intel SGX SVN value in the ACM's header, and if bit 0 of IA32_SGX_SVN_STATUS is 1, then the
OS/VMM should not launch that version of the ACM. It should obtain an updated version of the ACM either from
the BIOS or from an external resource.
However, OSVs/VMMs are strongly advised to update their version of the ACM any time they detect that the Intel
SGX SVN of the ACM carried by the OS/VMM is lower than that reported by IA32_SGX_SVN_STATUS MSR, irrespec-
tive of the setting of the lock bit.
42.12 INTERACTIONS
WITH
CACHING
OF LINEAR-ADDRESS TRANSLATIONS
Entering and exiting an enclave causes the logical processor to flush all the global linear-address context as well as
the linear-address context associated with the current VPID and PCID. The MONITOR FSM is also cleared.
42.13 INTERACTIONS WITH INTEL® TRANSACTIONAL SYNCHRONIZATION
EXTENSIONS (INTEL® TSX)
1. ENCLU or ENCLS instructions inside an HLE region will cause the flow to be aborted and restarted non-specula-
tively. ENCLU or ENCLS instructions inside an RTM region will cause the flow to be aborted and transfer control to
the fallback handler.
2. If XBEGIN is executed inside an enclave, the processor does NOT check whether the address of the fallback
handler is within the enclave.
3. If an RTM transaction is executing inside an enclave and there is an attempt to fetch an instruction outside the
enclave, the transaction is aborted and control is transferred to the fallback handler. No #GP is delivered.
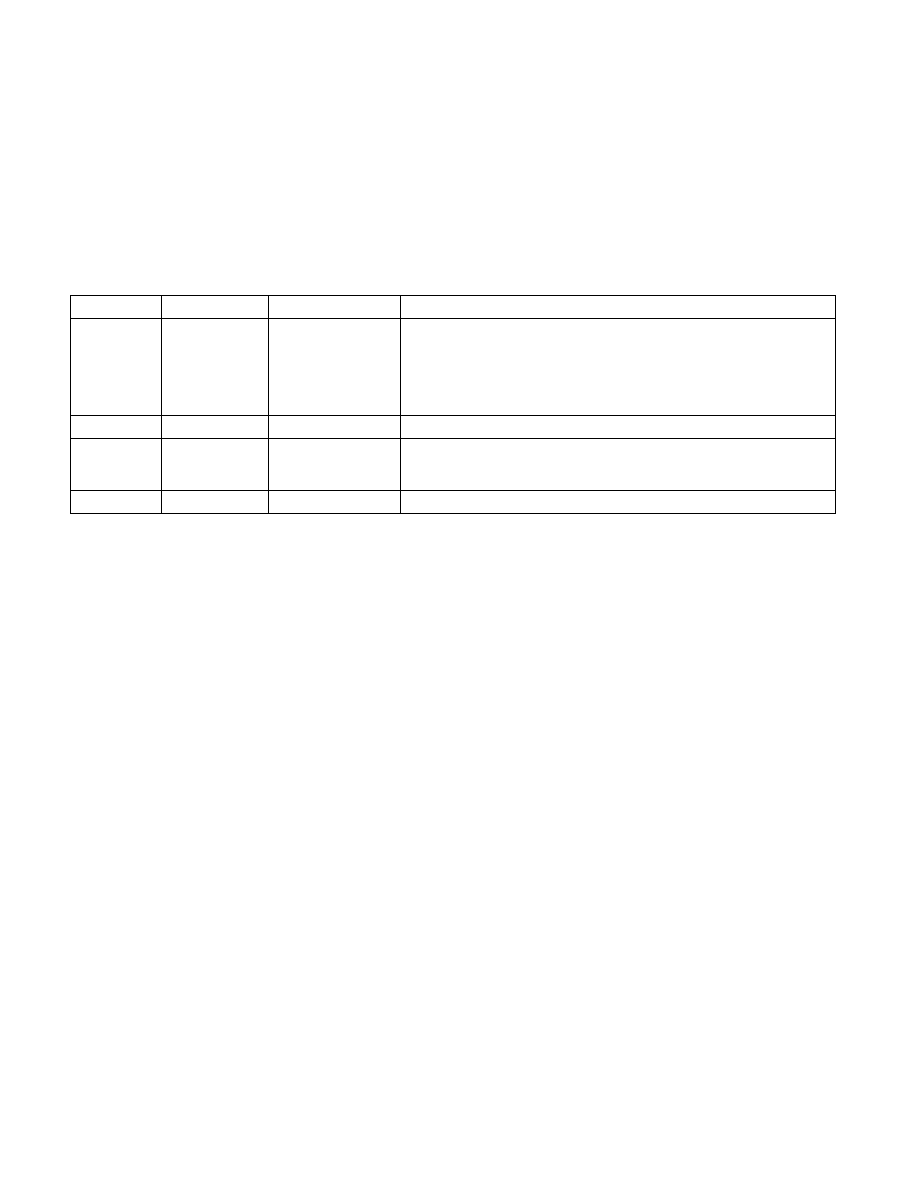
Table 42-2. Layout of the IA32_SGX_SVN_STATUS MSR
Bit Position
Name
ACM Module ID
Value
0
Lock
N.A.
• If 1, indicates that a non-faulting Intel SGX instruction has been
executed, consequently, launching a properly signed ACM but with Intel
SGX SVN value less than the BIOS specified Intel SGX SVN threshold
would lead to an TXT shutdown.
• If 0, indicates that the processor will allow a properly signed ACM to
launch irrespective of the Intel SGX SVN value of the ACM.
15:1
RSVD N.A.
0
23:16
SGX_SVN_SINIT SINIT ACM
• If CPUID.01H:ECX.SMX =1, this field reflects the expected threshold of
Intel SGX SVN for the SINIT ACM.
• If CPUID.01H:ECX.SMX =0, this field is reserved (0).
63:24
RSVD N.A.
0