Vol. 3A 3-5
PROTECTED-MODE MEMORY MANAGEMENT
Access checks can be used to protect not only against referencing an address outside the limit of a segment, but
also against performing disallowed operations in certain segments. For example, since code segments are desig-
nated as read-only segments, hardware can be used to prevent writes into code segments. The access rights infor-
mation created for segments can also be used to set up protection rings or levels. Protection levels can be used to
protect operating-system procedures from unauthorized access by application programs.
3.2.4
Segmentation in IA-32e Mode
In IA-32e mode of Intel 64 architecture, the effects of segmentation depend on whether the processor is running
in compatibility mode or 64-bit mode. In compatibility mode, segmentation functions just as it does using legacy
16-bit or 32-bit protected mode semantics.
In 64-bit mode, segmentation is generally (but not completely) disabled, creating a flat 64-bit linear-address
space. The processor treats the segment base of CS, DS, ES, SS as zero, creating a linear address that is equal to
the effective address. The FS and GS segments are exceptions. These segment registers (which hold the segment
base) can be used as additional base registers in linear address calculations. They facilitate addressing local data
and certain operating system data structures.
Note that the processor does not perform segment limit checks at runtime in 64-bit mode.
3.2.5
Paging and Segmentation
Paging can be used with any of the segmentation models described in Figures 3-2, 3-3, and 3-4. The processor’s
paging mechanism divides the linear address space (into which segments are mapped) into pages (as shown in
Figure 3-1). These linear-address-space pages are then mapped to pages in the physical address space. The
paging mechanism offers several page-level protection facilities that can be used with or instead of the segment-
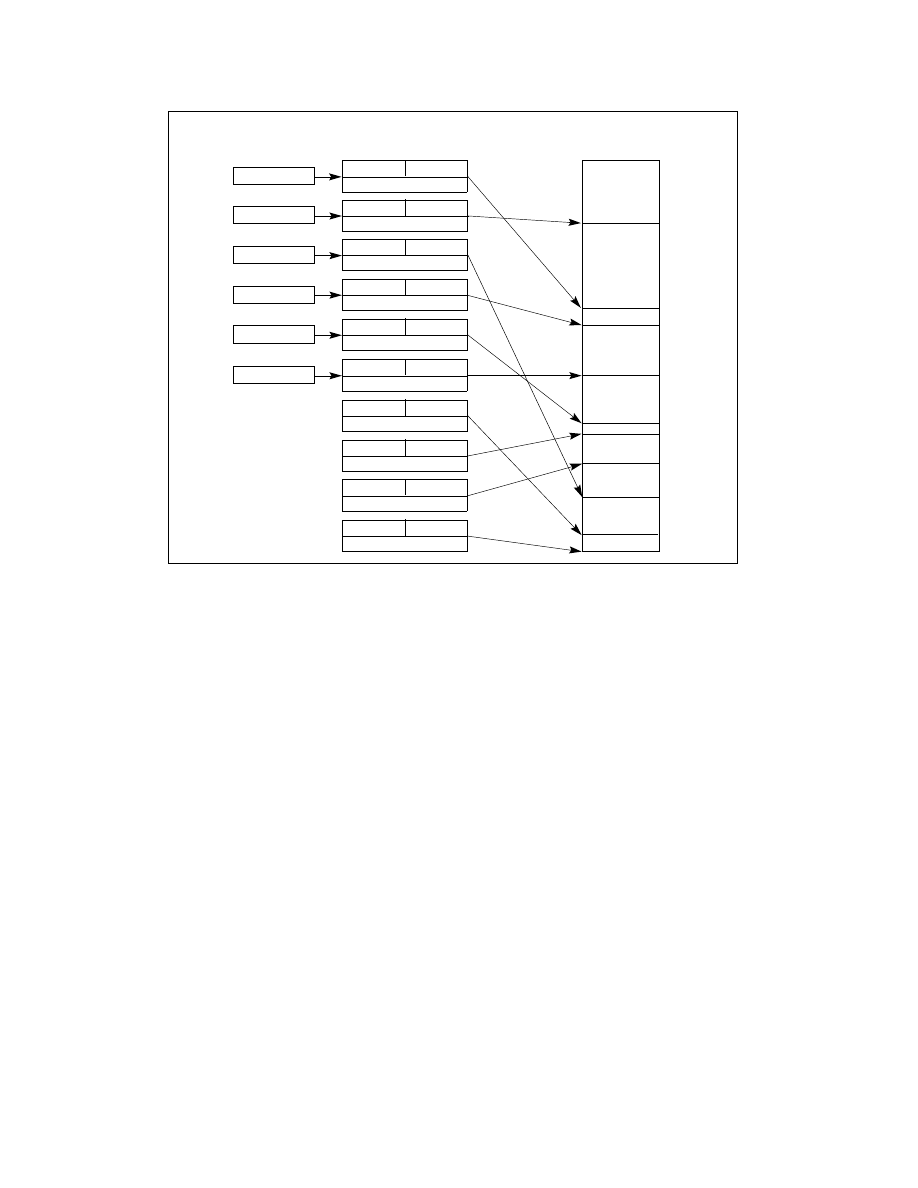
Figure 3-4. Multi-Segment Model
Linear Address Space
(or Physical Memory)
Segment
Registers
CS
Segment
Descriptors
Limit
Access
Base Address
SS
Limit
Access
Base Address
DS
Limit
Access
Base Address
ES
Limit
Access
Base Address
FS
Limit
Access
Base Address
GS
Limit
Access
Base Address
Limit
Access
Base Address
Limit
Access
Base Address
Limit
Access
Base Address
Limit
Access
Base Address
Stack
Code
Data
Data
Data
Data