Vol. 3B 17-53
DEBUG, BRANCH PROFILE, TSC, AND RESOURCE MONITORING FEATURES
The following sections describe extensions of CAT such as Code and Data Prioritization (CDP), followed by details
on specific features such as L3 CAT, L3 CDP, and L2 CAT. Depending on the specific processor a mix of features may
be supported, and CPUID provides enumeration capabilities to enable software to detect the set of supported
features.
17.17.2 Code and Data Prioritization (CDP) Technology
Code and Data Prioritization Technology is an extension of CAT. CDP enables isolation and separate prioritization of
code and data fetches to the L3 cache in a software configurable manner, which can enable workload prioritization
and tuning of cache capacity to the characteristics of the workload. CDP extends Cache Allocation Technology (CAT)
by providing separate code and data masks per Class of Service (COS).
By default, CDP is disabled on the processor. If the CAT MSRs are used without enabling CDP, the processor oper-
ates in a traditional CAT-only mode. When CDP is enabled,
•
the CAT mask MSRs are re-mapped into interleaved pairs of mask MSRs for data or code fetches (see
Figure 17-29),
•
the range of COS for CAT is re-indexed, with the lower-half of the COS range available for CDP.
Using the CDP feature, virtual isolation between code and data can be configured on the L3 cache if desired, similar
to how some processor cache levels provide separate L1 data and L1 instruction caches.
Like the CAT feature, CDP may be dynamically configured by privileged software at any point during normal system
operation, including dynamically enabling or disabling the feature provided that certain software configuration
requirements are met (see Section 17.17.4).
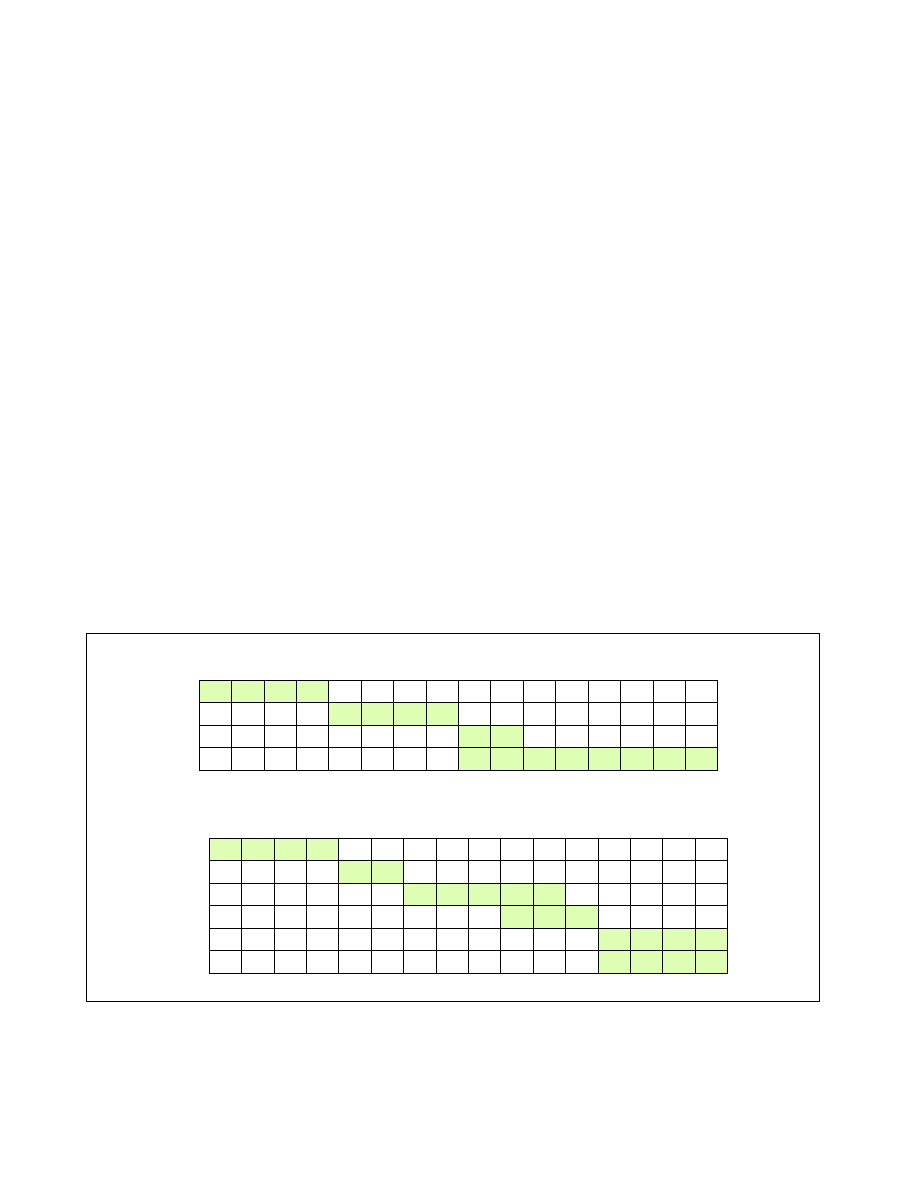
An example of the operating mode of CDP is shown in Figure 17-29. Shown at the top are traditional CAT usage
models where capacity masks map 1:1 with a COS number to enable control over the cache space which a given
COS (and thus applications, threads or VMs) may occupy. Shown at the bottom are example mask configurations
where CDP is enabled, and each COS number maps 1:2 to two masks, one for code and one for data. This enables
code and data to be either overlapped or isolated to varying degrees either globally or on a per-COS basis,
depending on application and system needs.
Figure 17-29. Code and Data Capacity Bitmasks of CDP
1
1
1
1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
1
1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
1
1
1
1
1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
1
1
1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
1
1
1
1
0
0
0
0
0
0
0
0
0
0
0
0
1
1
1
1
COS0.Data
COS0.Code
COS1.Data
COS1.Code
CAT with
1
1
1
1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
1
1
1
1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
1
1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
1
1
1
1
1
1
1
1
COS0
COS1
COS2
COS3
Traditional
CAT
CDP
Other COS.Data
Example of Code/Data Prioritization Usage - 16 bit Capacity Masks
Example of CAT-Only Usage - 16 bit Capacity Masks
Other COS.Code