Vol. 3D 37-1
INTRODUCTION TO INTEL® SOFTWARE GUARD EXTENSIONS
CHAPTER 37
INTRODUCTION TO INTEL® SOFTWARE GUARD EXTENSIONS
37.1 OVERVIEW
Intel
®
Software Guard Extensions (Intel
®
SGX) is a set of instructions and mechanisms for memory accesses
added to Intel
®
Architecture processors. Intel SGX can encompass two collections of instruction extensions,
referred to as SGX1 and SGX2, see Table 37-4. The SGX1 extensions allow an application to instantiate a protected
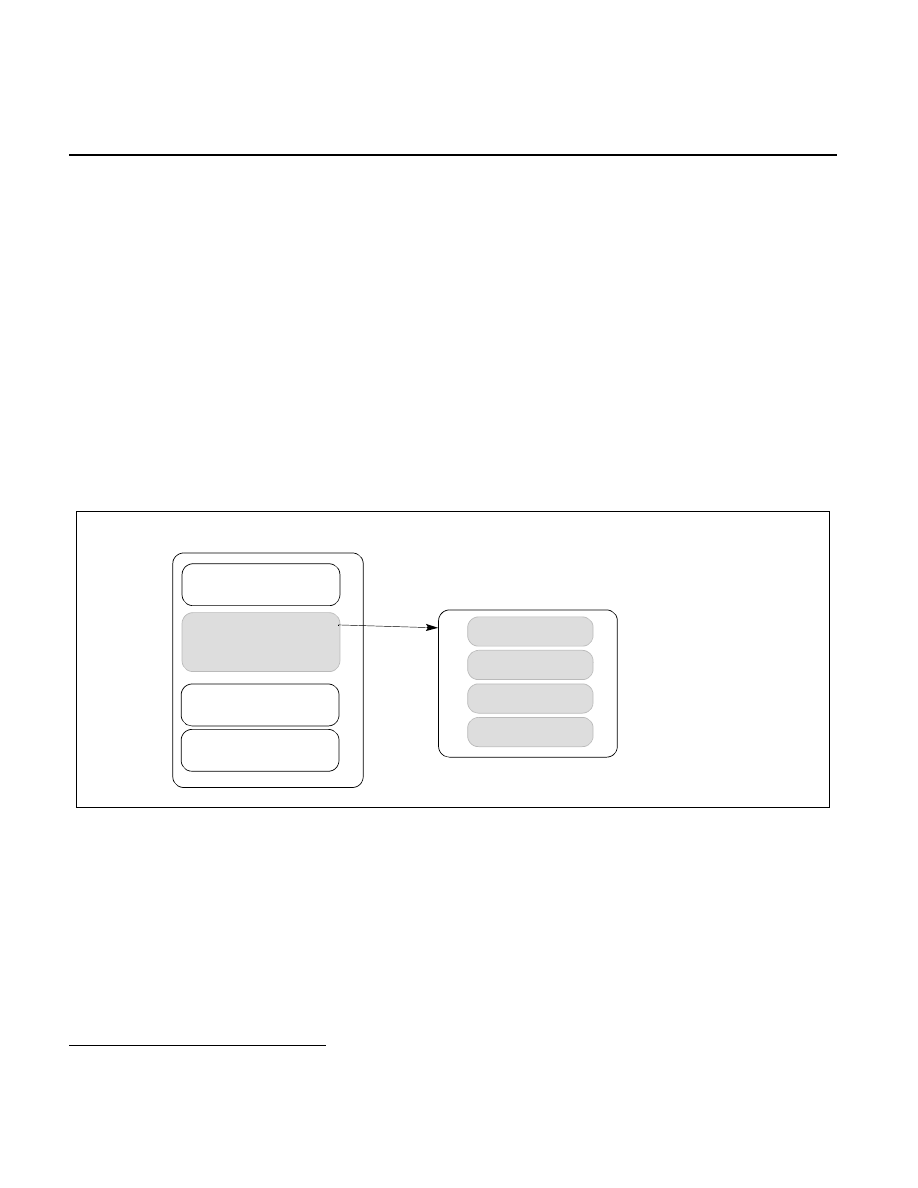
container, referred to as an enclave. An enclave is a protected area in the application’s address space (see
Figure 37-1), which provides confidentiality and integrity even in the presence of privileged malware. Accesses to
the enclave memory area from any software not resident in the enclave are prevented. The SGX2 extensions allow
additional flexibility in runtime management of enclave resources and thread execution within an enclave.
Chapter 38 covers main concepts, objects and data structure formats that interact within the Intel SGX architec-
ture. Chapter 39 covers operational aspects ranging from preparing an enclave, transferring control to enclave
code, and programming considerations for the enclave code and system software providing support for enclave
execution. Chapter 40 describes the behavior of Asynchronous Enclave Exit (AEX) caused by events while
executing enclave code. Chapter 41 covers the syntax and operational details of the instruction and associated leaf
functions available in Intel SGX. Chapter 42 describes interaction of various aspects of IA32 and Intel
®
64 archi-
tectures with Intel SGX. Chapter 43 covers Intel SGX support for application debug, profiling and performance
monitoring.
37.2
ENCLAVE INTERACTION AND PROTECTION
Intel SGX allows the protected portion of an application to be distributed in the clear. Before the enclave is built, the
enclave code and data are free for inspection and analysis. The protected portion is loaded into an enclave where
its code and data is measured. Once the application’s protected portion of the code and data are loaded into an
enclave, it is protected against external software access. An enclave can prove its identity to a remote party and
provide the necessary building-blocks for secure provisioning of keys and credentials. The application can also
request an enclave-specific and platform-specific key that it can use to protect keys and data that it wishes to store
outside the enclave.
1
Figure 37-1. An Enclave Within the Application’s Virtual Address Space
1. For additional information, see white papers on Intel SGX at http://software.intel.com/en-us/intel-isa-extensions.
OS
App Code
App Code
Entry Table
Enclave
Enclave Heap
Enclave Stack
Enclave Code