27-10 Vol. 3C
VM EXITS
— VM exits due to EPT violations that set bit 7 of the exit qualification (see Table 27-7; these are all EPT
violations except those resulting from an attempt to load the PDPTEs as of execution of the MOV CR
instruction). The linear address may translate to the guest-physical address whose access caused the EPT
violation. Alternatively, translation of the linear address may reference a paging-structure entry whose
access caused the EPT violation. Bits 63:32 are cleared if the logical processor was not in 64-bit mode
before the VM exit.
If the EPT violation occurred during execution of an instruction in enclave mode (and not during delivery of
an event incident to enclave mode), bits 11:0 of this field are cleared.
— For all other VM exits, the field is undefined.
•
Guest-physical address. For a VM exit due to an EPT violation or an EPT misconfiguration, this field receives
the guest-physical address that caused the EPT violation or EPT misconfiguration. For all other VM exits, the
field is undefined.
If the EPT violation or EPT misconfiguration occurred during execution of an instruction in enclave mode (and
not during delivery of an event incident to enclave mode), bits 11:0 of this field are cleared.
27.2.2
Information for VM Exits Due to Vectored Events
Section 24.9.2 defines fields containing information for VM exits due to the following events: exceptions (including
those generated by the instructions INT3, INTO, BOUND, and UD2); external interrupts that occur while the
“acknowledge interrupt on exit” VM-exit control is 1; and non-maskable interrupts (NMIs). Such VM exits include
those that occur on an attempt at a task switch that causes an exception before generating the VM exit due to the
task switch that causes the VM exit.
The following items detail the use of these fields:
•
VM-exit interruption information (format given in Table 24-15). The following items detail how this field is
established for VM exits due to these events:
— For an exception, bits 7:0 receive the exception vector (at most 31). For an NMI, bits 7:0 are set to 2. For
an external interrupt, bits 7:0 receive the vector.
— Bits 10:8 are set to 0 (external interrupt), 2 (non-maskable interrupt), 3 (hardware exception), or 6
(software exception). Hardware exceptions comprise all exceptions except breakpoint exceptions (#BP;
generated by INT3) and overflow exceptions (#OF; generated by INTO); these are software exceptions. (A
#BP that occurs in enclave mode is considered a hardware exception.) BOUND-range exceeded exceptions
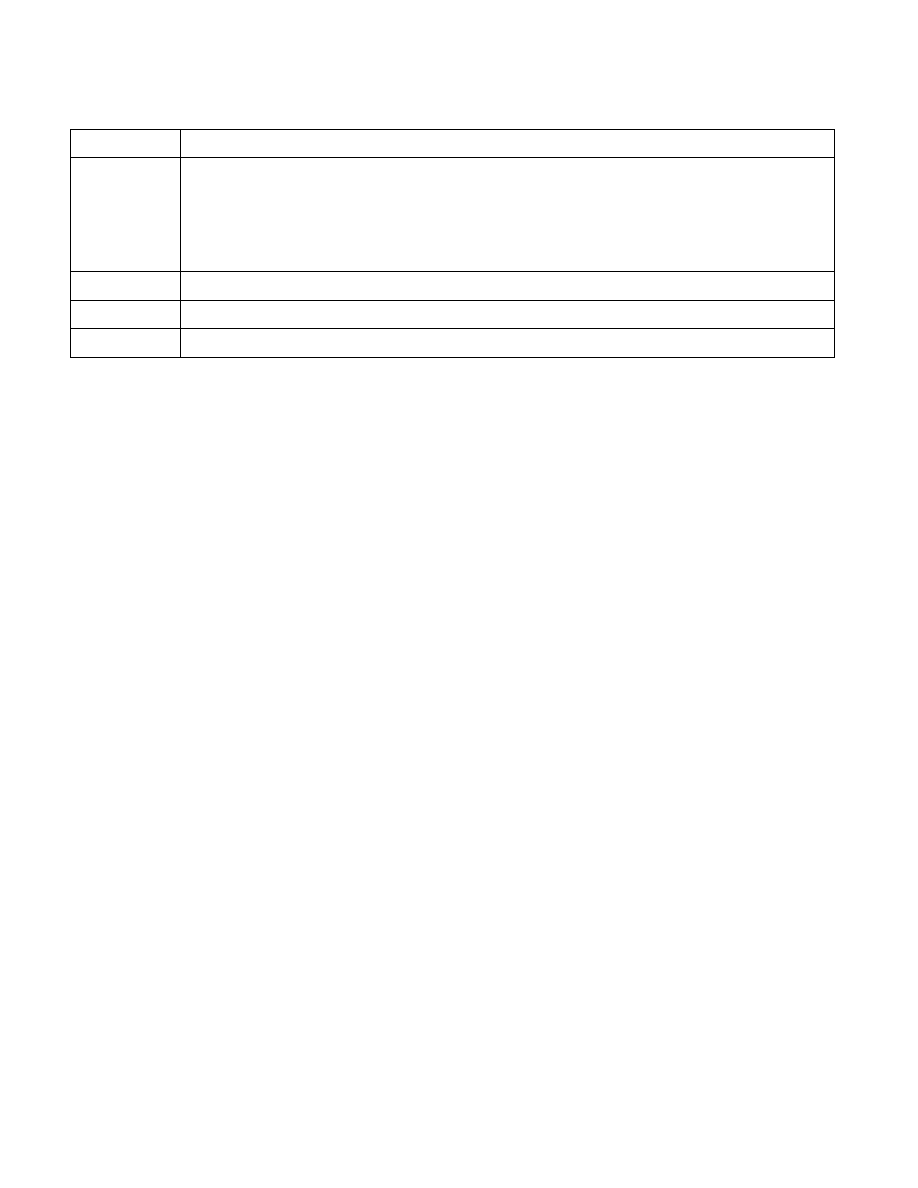
8
If bit 7 is 1:
• Set if the access causing the EPT violation is to a guest-physical address that is the translation of a linear
address.
• Clear if the access causing the EPT violation is to a paging-structure entry as part of a page walk or the
update of an accessed or dirty bit.
Reserved if bit 7 is 0 (cleared to 0).
11:9
Reserved (cleared to 0).
12
NMI unblocking due to IRET
63:13
Reserved (cleared to 0).
NOTES:
1. If accessed and dirty flags for EPT are enabled, processor accesses to guest paging-structure entries are treated as writes with
regard to EPT violations (see Section 28.2.3.2). If such an access causes an EPT violation, the processor sets both bit 0 and bit 1 of
the exit qualification.
2. Bits 5:3 are cleared to 0 if any of EPT paging-structure entries used to translate the guest-physical address of the access causing the
EPT violation is not present (see Section 28.2.2).
Table 27-7. Exit Qualification for EPT Violations (Contd.)
Bit Position(s)
Contents