Vol. 3A 9-37
PROCESSOR MANAGEMENT AND INITIALIZATION
9.11.7.2 Authenticating the Update
An update may be authenticated by the BIOS using the signature primitive, described above, and the algorithm in
Example 9-10.
Example 9-10. Pseudo Code to Authenticate the Update
Z
← Obtain Update Revision from the Update Header to be authenticated;
X
← Obtain Current Update Signature from MSR 8BH;
If (Z > X)
{
Load Update that is to be authenticated;
Y
← Obtain New Signature from MSR 8BH;
If (Z = Y)
Success
Else
Fail
}
Else
Fail
Example 9-10 requires that the BIOS only authenticate updates that contain a numerically larger revision than the
currently loaded revision, where Current Signature (X) < New Update Revision (Z). A processor with no loaded
update is considered to have a revision equal to zero.
This authentication procedure relies upon the decoding provided by the processor to verify an update from a poten-
tially hostile source. As an example, this mechanism in conjunction with other safeguards provides security for
dynamically incorporating field updates into the BIOS.
9.11.8
Optional Processor Microcode Update Specifications
This section an interface that an OEM-BIOS may provide to its client system software to manage processor micro-
code updates. System software may choose to build its own facility to manage microcode updates (e.g. similar to
the facility described in Section 9.11.6) or rely on a facility provided by the BIOS to perform microcode updates.
Sections 9.11.8.1-9.11.8.9 describes an extension (Function 0D042H) to the real mode INT 15H service. INT 15H
0D042H function is one of several alternatives that a BIOS may choose to implement microcode update facility and
offer to its client application (e.g. an OS). Other alternative microcode update facility that BIOS can choose are
dependent on platform-specific capabilities, including the Capsule Update mechanism from the UEFI specification
(www.uefi.org). In this discussion, the application is referred to as the calling program or caller.
The real mode INT15 call specification described here is an Intel extension to an OEM BIOS. This extension allows
an application to read and modify the contents of the microcode update data in NVRAM. The update loader, which
is part of the system BIOS, cannot be updated by the interface. All of the functions defined in the specification must
be implemented for a system to be considered compliant with the specification. The INT15 functions are accessible
only from real mode.
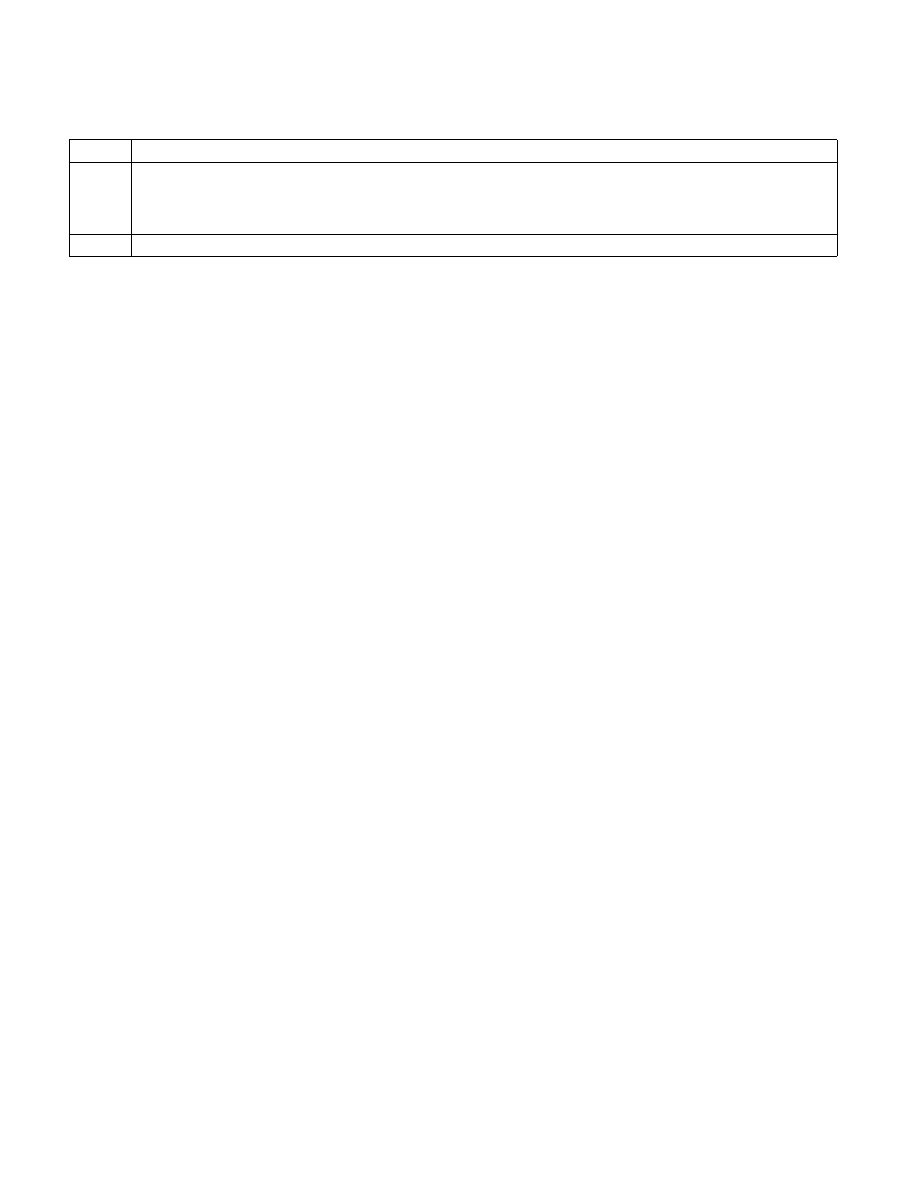
Table 9-12. Microcode Update Signature
Bit
Description
63:32
Microcode update signature. This field contains the signature of the currently loaded microcode update when read following
the execution of the CPUID instruction, function 1. It is required that this register field be pre-loaded with zero prior to
executing the CPUID, function 1. If the field remains equal to zero, then there is no microcode update loaded. Another non-
zero value will be the signature.
31:0
Reserved.