Vol. 3D 39-13
ENCLAVE OPERATION
39.5.11 Extending the EPCM Permissions of a Page
On processors that support SGX2, extending the EPCM permissions associated with an enclave page is accom-
plished directly be the enclave using the EMODPE leaf function. After performing the EPCM permission extension,
the enclave requests the OS to update the page table permissions to match the extended permission. Security
wise, permission extension does not require enclave threads to leave the enclave as TLBs with stale references to
the more restrictive permissions will be flushed on demand, but to allow forward progress, an OS needs to be
aware that an application might signal a page fault.
The typical process for extending the permissions of an enclave page is as follows:
1. Enclave invokes EMODPE to extend the EPCM permissions associated with an EPC page (EMODPE may only be
called on VALID pages).
2. Enclave requests that OS update the page tables to match the new EPCM permissions.
3. Enclave code resumes.
a. If cached linear-address to physical-address translations are present to the more restrictive permissions,
the enclave thread will page fault. The SGX2-aware OS will see that the page tables permit the access and
resume the thread, which can now successfully access the page because exiting cleared the TLB.
b. If cached linear-address to physical-address translations are not present, access to the page with the new
permissions will succeed without an enclave exit.
39.6
CHANGES TO INSTRUCTION BEHAVIOR INSIDE AN ENCLAVE
This section covers instructions whose behavior changes when executed in enclave mode.
39.6.1 Illegal
Instructions
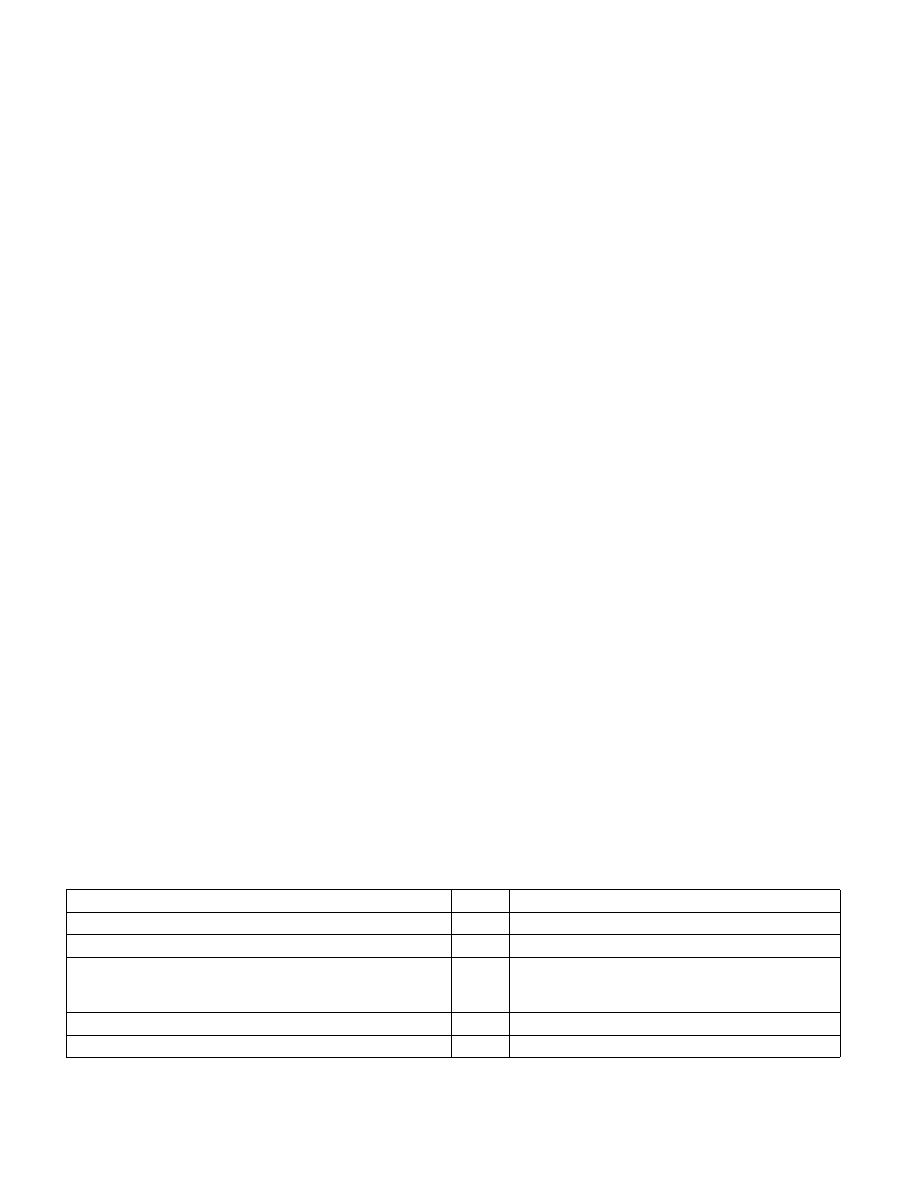
The instructions listed in Table 39-1 are ring 3 instructions which become illegal when executed inside an enclave.
Executing these instructions inside an enclave will generate an exception.
The first row of Table 39-1 enumerates instructions that may cause a VM exit for VMM emulation. Since a VMM
cannot emulate enclave execution, execution of any these instructions inside an enclave results in an invalid-
opcode exception (#UD) and no VM exit.
The second row of Table 39-1 enumerates I/O instructions that may cause a fault or a VM exit for emulation. Again,
enclave execution cannot be emulated, so execution of any these instructions inside an enclave results in #UD.
The third row of Table 39-1 enumerates instructions that load descriptors from the GDT or the LDT or that change
privilege level. The former class is disallowed because enclave software should not depend on the contents of the
descriptor tables and the latter because enclave execution must be entirely with CPL = 3. Again, execution of any
these instructions inside an enclave results in #UD.
The fourth row of Table 39-1 enumerates instructions that provide access to kernel information from user mode
and can be used to aid kernel exploits from within enclave. Execution of any these instructions inside an enclave
results in #UD
Table 39-1. Illegal Instructions Inside an Enclave
Instructions
Result
Comment
CPUID, GETSEC, RDPMC, SGDT, SIDT, SLDT, STR, VMCALL, VMFUNC #UD
Might cause VM exit.
IN, INS/INSB/INSW/INSD, OUT, OUTS/OUTSB/OUTSW/OUTSD
#UD
I/O fault may not safely recover. May require emulation.
Far call, Far jump, Far Ret, INT n/INTO, IRET, LDS/LES/LFS/LGS/LSS,
MOV to DS/ES/SS/FS/GS, POP DS/ES/SS/FS/GS, SYSCALL,
SYSENTER
#UD
Access segment register could change privilege level.
SMSW
#UD
Might provide access to kernel information.
ENCLU[EENTER], ENCLU[ERESUME]
#GP
Cannot enter an enclave from within an enclave.