39-8 Vol. 3D
ENCLAVE OPERATION
•
PROVISIONING Key and PROVISIONING SEAL Key: These keys are used by attestation key provisioning
software to prove to remote parties that the processor is genuine and identify the currently executing TCB.
These keys are only available to enclaves with ATTRIBUTE.PROVISIONKEY set to 1.
39.4.3.1 Sealing Enclave Data
Enclaves can protect persistent data using Seal keys to provide encryption and/or integrity protection. EGETKEY
provides two types of Seal keys specified in KEYREQUEST.KEYPOLICY field: MRENCLAVE-based key and
MRSIGNER-based key.
The MRENCLAVE-based keys are available only to enclave instances sharing the same MRENCLAVE. If a new
version of the enclave is released, the Seal keys will be different. Retrieving previous data requires additional soft-
ware support.
The MRSIGNER-based keys are bound to the 3 tuple (MRSIGNER, ISVPRODID, ISVSVN). These keys are available
to any enclave with the same MRSIGNER and ISVPRODID and an ISVSVN equal to or greater than the key in ques-
tions. This is valuable for allowing new versions of the same software to retrieve keys created before an upgrade.
39.4.3.2 Using REPORTs for Local Attestation
SGX provides a means for enclaves to securely identify one another, this is referred to as “Local Attestation”. SGX
provides a hardware assertion, REPORT that contains calling enclaves Attributes, Measurements and User supplied
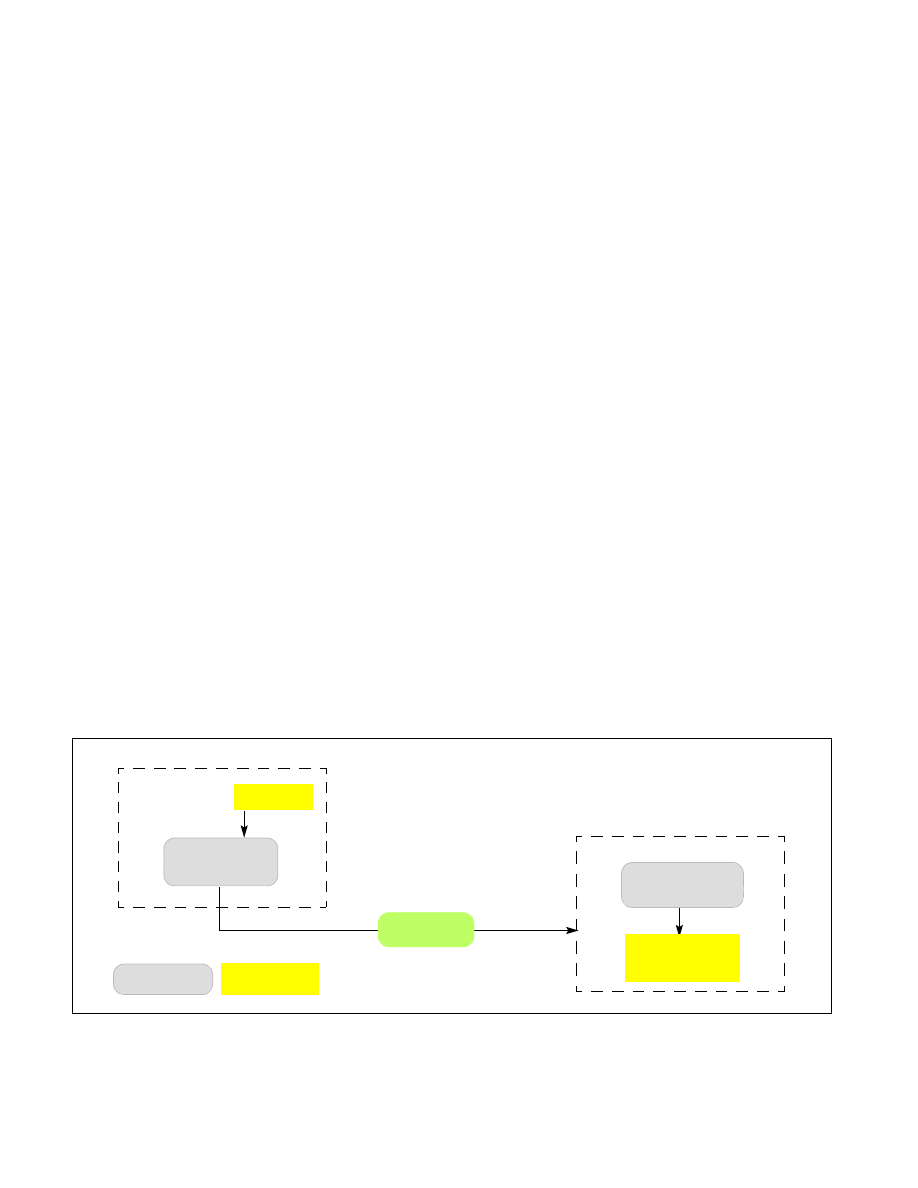
data (described in detail in Section 38.15). Figure 39-3 shows the basic flow of information.
1. The source enclave determines the identity of the target enclave to populate TARGETINFO.
2. The source enclave calls EREPORT instruction to generate a REPORT structure. The EREPORT instruction
conducts the following:
— Populates the REPORT with identify information about the calling enclave.
— Derives the Report Key that is returned when the target enclave executes the EGETKEY. TARGETINFO
provides information about the target.
— Computes a MAC over the REPORT using derived target enclave Report Key.
3. Non-enclave software copies the REPORT from source to destination.
4. The target enclave executes the EGETKEY instruction to request its REPORT key, which is the same key used by
EREPORT at the source.
5. The target enclave verifies the MAC and can then inspect the REPORT to identify the source.
Figure 39-3. SGX Local Attestation
EREPORT
REPORT
Software
Verify REPORT
(Symmetric Key)
Source Enclave
Destination Enclave
EGETKEY
REPORT KEY
(Symmetric Key)
Hardware
Legend:
TARGETINFO