5-26 Vol. 3A
PROTECTION
5.10.4
Checking Caller Access Privileges (ARPL Instruction)
The requestor’s privilege level (RPL) field of a segment selector is intended to carry the privilege level of a calling
procedure (the calling procedure’s CPL) to a called procedure. The called procedure then uses the RPL to determine
if access to a segment is allowed. The RPL is said to “weaken” the privilege level of the called procedure to that of
the RPL.
Operating-system procedures typically use the RPL to prevent less privileged application programs from accessing
data located in more privileged segments. When an operating-system procedure (the called procedure) receives a
segment selector from an application program (the calling procedure), it sets the segment selector’s RPL to the
privilege level of the calling procedure. Then, when the operating system uses the segment selector to access its
associated segment, the processor performs privilege checks using the calling procedure’s privilege level (stored in
the RPL) rather than the numerically lower privilege level (the CPL) of the operating-system procedure. The RPL
thus insures that the operating system does not access a segment on behalf of an application program unless that
program itself has access to the segment.
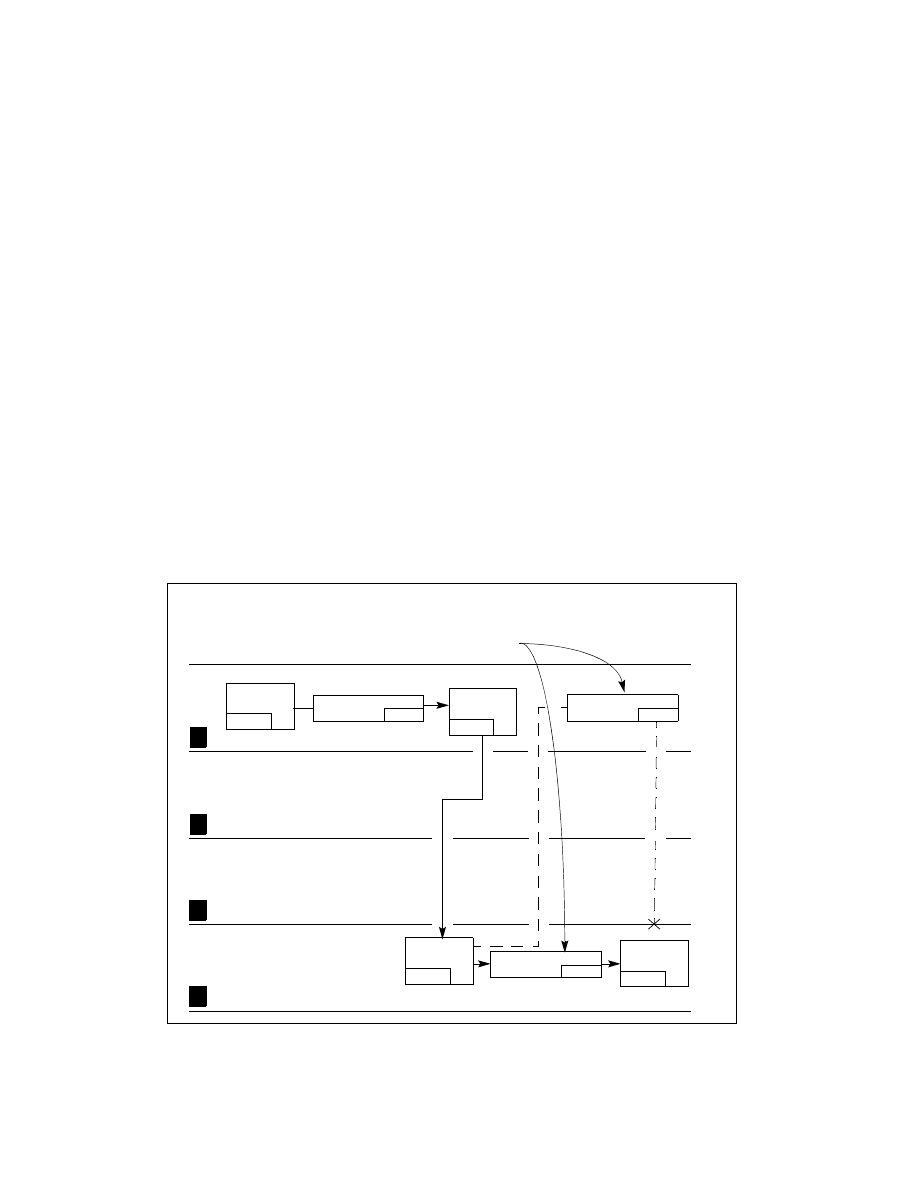
Figure 5-15 shows an example of how the processor uses the RPL field. In this example, an application program
(located in code segment A) possesses a segment selector (segment selector D1) that points to a privileged data
structure (that is, a data structure located in a data segment D at privilege level 0).
The application program cannot access data segment D, because it does not have sufficient privilege, but the oper-
ating system (located in code segment C) can. So, in an attempt to access data segment D, the application
program executes a call to the operating system and passes segment selector D1 to the operating system as a
parameter on the stack. Before passing the segment selector, the (well behaved) application program sets the RPL
of the segment selector to its current privilege level (which in this example is 3). If the operating system attempts
to access data segment D using segment selector D1, the processor compares the CPL (which is now 0 following
the call), the RPL of segment selector D1, and the DPL of data segment D (which is 0). Since the RPL is greater than
the DPL, access to data segment D is denied. The processor’s protection mechanism thus protects data segment D
from access by the operating system, because application program’s privilege level (represented by the RPL of
segment selector B) is greater than the DPL of data segment D.
Figure 5-15. Use of RPL to Weaken Privilege Level of Called Procedure
Passed as a
parameter on
the stack.
Access
allowed
Access
allowed
Application Program
Operating
System
Lowest Privilege
Highest Privilege
3
2
1
0
Data
Segment D
not
Segment Sel. D1
RPL=3
Segment Sel. D2
RPL=0
Gate Selector B
RPL=3
Code
Segment A
CPL=3
Code
Segment C
DPL=0
Call
Gate B
DPL=3
DPL=0