Vol. 3D 38-5
ENCLAVE ACCESS CONTROL AND DATA STRUCTURES
38.7.1 ATTRIBUTES
The ATTRIBUTES data structure is comprised of bit-granular fields that are used in the SECS, the REPORT and the
KEYREQUEST structures. CPUID.(EAX=12H, ECX=1) enumerates a bitmap of permitted 1-setting of bits in ATTRI-
BUTES.
38.7.2 SECS.MISCSELECT
Field
CPUID.(EAX=12H, ECX=0):EBX[31:0] enumerates which extended information that the processor can save into
the MISC region of SSA when an AEX occurs. An enclave writer can specify via SIGSTRUCT how to set the
SECS.MISCSELECT field. The bit vector of MISCSELECT selects which extended information is to be saved in the
MISC region of the SSA frame when an AEX is generated. The bit vector definition of extended information is listed
in Table 38-4.
If CPUID.(EAX=12H, ECX=0):EBX[31:0] = 0, SECS.MISCSELECT field must be all zeros.
The SECS.MISCSELECT field determines the size of MISC region of the SSA frame, see Section 38.9.2.
RESERVED
96
32
MRSIGNER
128
32
Measurement Register extended with the public key that verified the
enclave. See SIGSTRUCT for format.
RESERVED
160
96
ISVPRODID
256
2
Product ID of enclave.
ISVSVN
258
2
Security version number (SVN) of the enclave.
RESERVED
260
3836
The RESERVED field consists of the following:
• EID: An 8 byte Enclave Identifier. Its location is implementation specific.
• PAD: A 352 bytes padding pattern from the Signature (used for key
derivation strings). It’s location is implementation specific.
• The remaining 3476 bytes are reserved area.
The entire 3836 byte field must be cleared prior to executing ECREATE or
EREPORT.
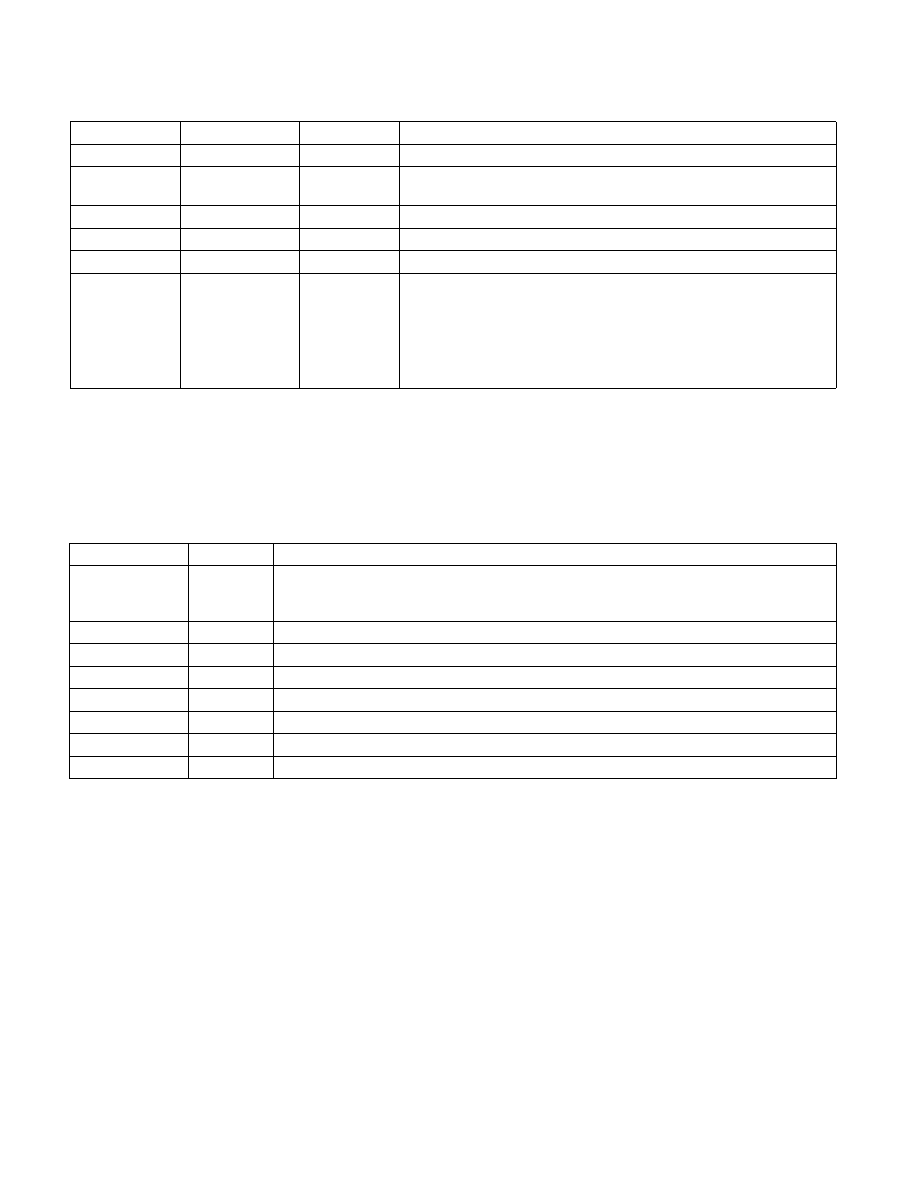
Table 38-3. Layout of ATTRIBUTES Structure
Field
Bit Position
Description
INIT
0
This bit indicates if the enclave has been initialized by EINIT. It must be cleared when loaded as
part of ECREATE. For EREPORT instruction, TARGET_INFO.ATTRIBUTES[ENIT] must always be 1 to
match the state after EINIT has initialized the enclave.
DEBUG
1
If 1, the enclave permit debugger to read and write enclave data using EDBGRD and EDBGWR.
MODE64BIT
2
Enclave runs in 64-bit mode.
RESERVED
3
Must be Zero.
PROVISIONKEY
4
Provisioning Key is available from EGETKEY.
EINITTOKENKEY
5
EINIT token key is available from EGETKEY.
RESERVED
63:6
XFRM
127:64
XSAVE Feature Request Mask. See Section 42.7.
Table 38-2. Layout of SGX Enclave Control Structure (SECS) (Contd.)
Field
OFFSET (Bytes)
Size (Bytes)
Description