Vol. 3D 38-3
ENCLAVE ACCESS CONTROL AND DATA STRUCTURES
Explicit accesses are always made using logical addresses. These accesses are subject to segmentation, paging,
extended paging, and APIC-virtualization checks, and trigger any faults/exit associated with these checks when the
access is made.
The interaction of explicit memory accesses with data breakpoints is leaf-function-specific, and is documented in
Section 43.3.4.
38.5.3.2 Implicit Accesses
Accesses to data structures whose physical addresses are cached by the processor are called implicit accesses.
These addresses are not passed as operands of the instruction but are implied by use of the instruction.
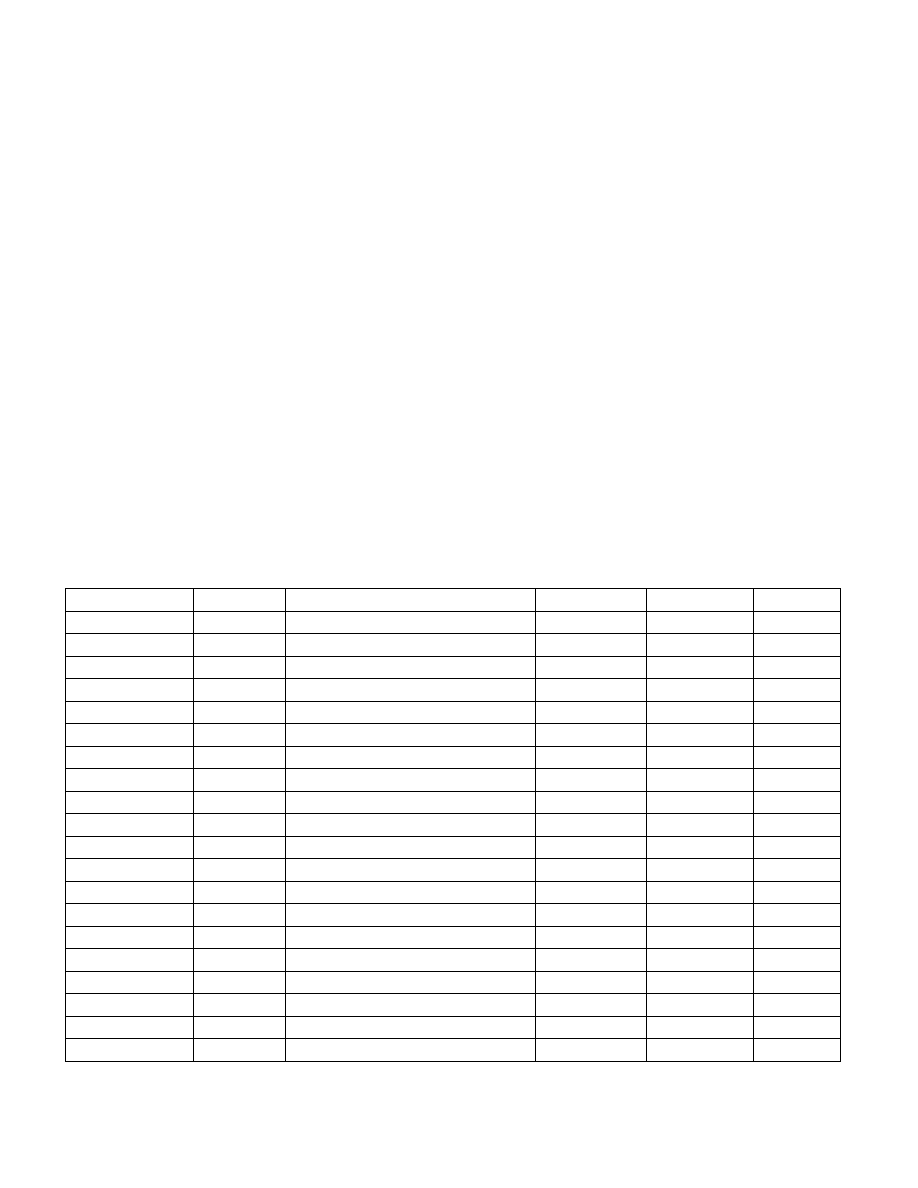
These accesses do not trigger any access-control faults/exits or data breakpoints. Table 38-1 lists memory objects
that Intel SGX instruction leaf functions access either by explicit access or implicit access. The addresses of explicit
access objects are passed via register operands with the second through fourth column of Table 38-1 matching
implicitly encoded registers RBX, RCX, RDX.
Physical addresses used in different implicit accesses are cached via different instructions and for different dura-
tions. The physical address of SECS associated with each EPC page is cached at the time the page is added to the
enclave via ENCLS[EADD] or ENCLS[EAUG], or when the page is loaded to EPC via ENCLS[ELDB] or ENCLS[ELDU].
This binding is severed when the corresponding page is removed from the EPC via ENCLS[EREMOVE] or
ENCLS[EWB]. Physical addresses of TCS and SSA pages are cached at the time of most-recent enclave entry. Exit
from an enclave (ENCLU[EEXIT] or AEX) flushes this caching. Details of Asynchronous Enclave Exit is described in
Chapter 40.
The physical addresses that are cached for use by implicit accesses are derived from logical (or linear) addresses
after checks such as segmentation, paging, EPT, and APIC virtualization checks. These checks may trigger excep-
tions or VM exits. Note, however, that such exception or VM exits may not occur after a physical address is cached
and used for an implicit access.
Table 38-1. List of Implicit and Explicit Memory Access by Intel® SGX Enclave Instructions
Instr. Leaf
Enum.
Explicit 1
Explicit 2
Explicit 3
Implicit
EACCEPT
SGX2
SECINFO
EPCPAGE
SECS
EACCEPTCOPY
SGX2
SECINFO
EPCPAGE (Src)
EPCPAGE (Dst)
EADD
SGX1
PAGEINFO and linked structures
EPCPAGE
EAUG
SGX2
PAGEINFO and linked structures
EPCPAGE
SECS
EBLOCK
SGX1
EPCPAGE
SECS
ECREATE
SGX1
PAGEINFO and linked structures
EPCPAGE
EDBGRD
SGX1
EPCADDR
Destination
SECS
EDBGWR
SGX1
EPCADDR
Source
SECS
EENTER
SGX1
TCS and linked SSA
SECS
EEXIT
SGX1
SECS, TCS
EEXTEND
SGX1
SECS
EPCPAGE
EGETKEY
SGX1
KEYREQUEST
KEY
SECS
EINIT
SGX1
SIGSTRUCT
SECS
EINITTOKEN
ELDB/ELDU
SGX1
PAGEINFO and linked structures, PCMD
EPCPAGE
VAPAGE
EMODPE
SGX2
SECINFO
EPCPAGE
EMODPR
SGX2
SECINFO
EPCPAGE
SECS
EMODT
SGX2
SECINFO
EPCPAGE
SECS
EPA
SGX1
EPCADDR
EREMOVE
SGX1
EPCPAGE
SECS
EREPORT
SGX1
TARGETINFO
REPORTDATA
OUTPUTDATA
SECS