Vol. 3D 37-3
INTRODUCTION TO INTEL® SOFTWARE GUARD EXTENSIONS
is accessible to the program currently executing. Generally an EPC page is only accessed by the owner of the
executing enclave or an instruction which is setting up an EPC page
The EPC is divided into EPC pages. An EPC page is 4KB in size and always aligned on a 4KB boundary.
Pages in the EPC can either be valid or invalid. Every valid page in the EPC belongs to one enclave instance. Each
enclave instance has an EPC page that holds its SECS. The security metadata for each EPC page is held in an
internal micro-architectural structure called Enclave Page Cache Map (EPCM, see Section 37.5.1).
The EPC is managed by privileged software. Intel SGX provides a set of instructions for adding and removing
content to and from the EPC. The EPC may be configured by BIOS at boot time. On implementations in which EPC
memory is part of system DRAM, the contents of the EPC are protected by an encryption engine.
37.5.1
Enclave Page Cache Map (EPCM)
The EPCM is a secure structure used by the processor to track the contents of the EPC. The EPCM holds one entry
for each page in the EPC. The format of the EPCM is micro-architectural, and consequently is implementation
dependent. However, the EPCM contains the following architectural information:
•
The status of EPC page with respect to validity and accessibility.
•
An SECS identifier (see Section 38.19) of the enclave to which the page belongs.
•
The type of page: regular, SECS, TCS or VA.
•
The linear address through which the enclave is allowed to access the page.
•
The specified read/write/execute permissions on that page.
The EPCM structure is used by the CPU in the address-translation flow to enforce access-control on the EPC pages.
The EPCM structure is described in Table 38-27, and the conceptual access-control flow is described in Section
38.5.
The EPCM entries are managed by the processor as part of various instruction flows.
37.6
ENCLAVE INSTRUCTIONS AND INTEL® SGX
The enclave instructions available with Intel SGX are organized as leaf functions under two instruction mnemonics:
ENCLS (ring 0) and ENCLU (ring 3). Each leaf function uses EAX to specify the leaf function index, and may require
additional implicit input registers as parameters. The use of EAX is implied implicitly by the ENCLS and ENCLU
instructions, ModR/M byte encoding is not used with ENCLS and ENCLU. The use of additional registers does not
use ModR/M encoding and is implied implicitly by the respective leaf function index.
Each leaf function index is also associated with a unique, leaf-specific mnemonic. A long-form expression of Intel
SGX instruction takes the form of ENCLx[LEAF_MNEMONIC], where ‘x’ is either ‘S’ or ‘U’. The long-form expression
provides clear association of the privilege-level requirement of a given “leaf mnemonic”. For simplicity, the unique
“Leaf_Mnemonic” name is used (omitting the ENCLx for convenience) throughout in this document.
Details of Individual SGX leaf functions are described in Chapter 41. Table 37-1 provides a summary of the instruc-
tion leaves that are available in the initial implementation of Intel SGX, which is introduced in the 6th generation
Intel Core processors. Table 37-1 summarizes enhancement of Intel SGX for future Intel processors.
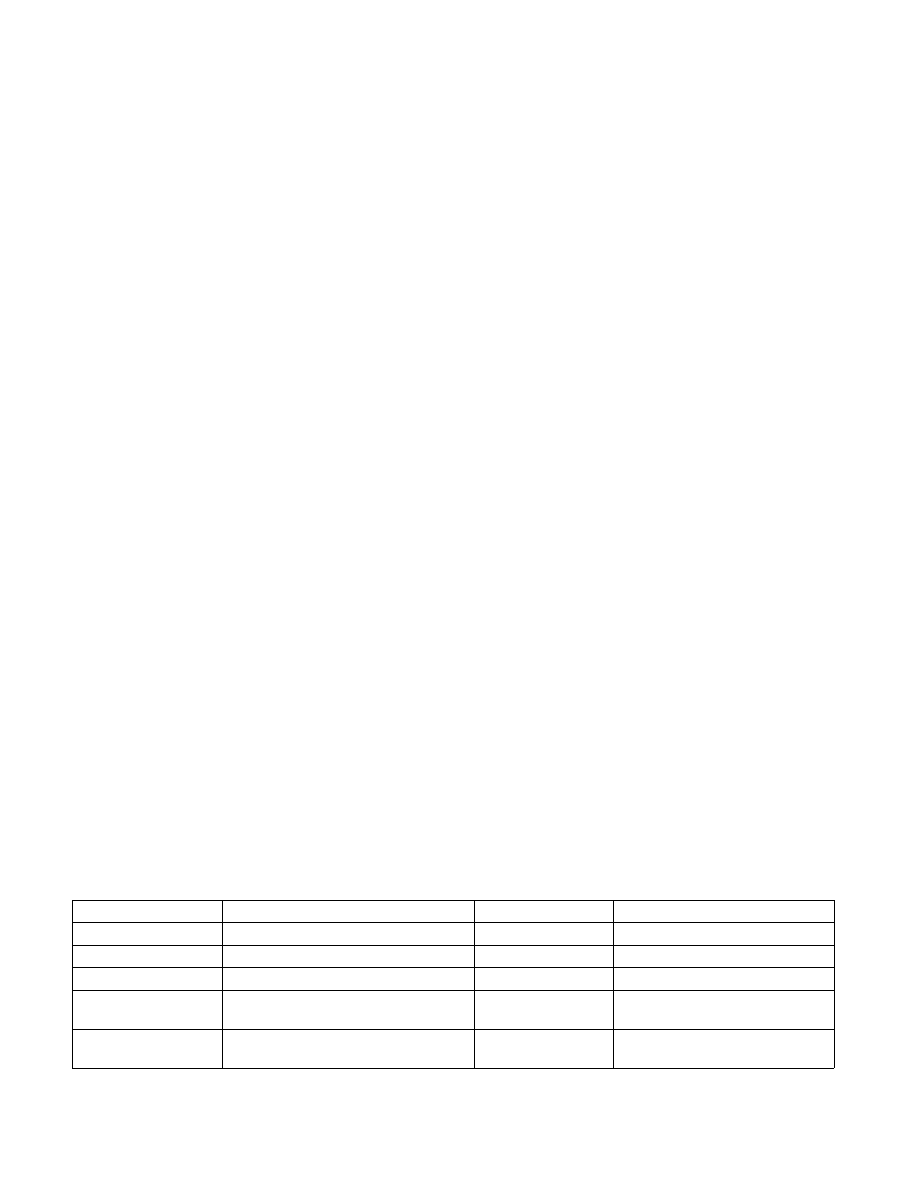
Table 37-1. Supervisor and User Mode Enclave Instruction Leaf Functions in Long-Form of SGX1
Supervisor Instruction
Description
User Instruction
Description
ENCLS[EADD]
Add an EPC page to an enclave.
ENCLU[EENTER]
Enter an enclave.
ENCLS[EBLOCK]
Block an EPC page.
ENCLU[EEXIT]
Exit an enclave.
ENCLS[ECREATE]
Create an enclave.
ENCLU[EGETKEY]
Create a cryptographic key.
ENCLS[EDBGRD]
Read data from a debug enclave by debug-
ger.
ENCLU[EREPORT]
Create a cryptographic report.
ENCLS[EDBGWR]
Write data into a debug enclave by debug-
ger.
ENCLU[ERESUME]
Re-enter an enclave.