CMPPS—Compare Packed Single-Precision Floating-Point Values
INSTRUCTION SET REFERENCE, A-L
3-162 Vol. 2A
VEX.128 encoded version: The first source operand (second operand) is an XMM register. The second source
operand (third operand) can be an XMM register or a 128-bit memory location. Bits (MAX_VL-1:128) of the desti-
nation ZMM register are zeroed. Four comparisons are performed with results written to bits 127:0 of the destina-
tion operand.
The comparison predicate operand is an 8-bit immediate:
•
For instructions encoded using the VEX prefix and EVEX prefix, bits 4:0 define the type of comparison to be
performed (see Table 3-1). Bits 5 through 7 of the immediate are reserved.
•
For instruction encodings that do not use VEX prefix, bits 2:0 define the type of comparison to be made (see the
first 8 rows of Table 3-1). Bits 3 through 7 of the immediate are reserved.
The unordered relationship is true when at least one of the two source operands being compared is a NaN; the
ordered relationship is true when neither source operand is a NaN.
A subsequent computational instruction that uses the mask result in the destination operand as an input operand
will not generate an exception, because a mask of all 0s corresponds to a floating-point value of +0.0 and a mask
of all 1s corresponds to a QNaN.
Note that processors with “CPUID.1H:ECX.AVX =0” do not implement the “greater-than”, “greater-than-or-equal”,
“not-greater than”, and “not-greater-than-or-equal relations” predicates. These comparisons can be made either
by using the inverse relationship (that is, use the “not-less-than-or-equal” to make a “greater-than” comparison)
or by using software emulation. When using software emulation, the program must swap the operands (copying
registers when necessary to protect the data that will now be in the destination), and then perform the compare
using a different predicate. The predicate to be used for these emulations is listed in the first 8 rows of Table 3-7
(Intel 64 and IA-32 Architectures Software Developer’s Manual Volume 2A) under the heading Emulation.
Compilers and assemblers may implement the following two-operand pseudo-ops in addition to the three-operand
CMPPS instruction, for processors with “CPUID.1H:ECX.AVX =0”. See Table 3-4. Compiler should treat reserved
Imm8 values as illegal syntax.
:
The greater-than relations that the processor does not implement require more than one instruction to emulate in
software and therefore should not be implemented as pseudo-ops. (For these, the programmer should reverse the
operands of the corresponding less than relations and use move instructions to ensure that the mask is moved to
the correct destination register and that the source operand is left intact.)
Processors with “CPUID.1H:ECX.AVX =1” implement the full complement of 32 predicates shown in Table 3-5, soft-
ware emulation is no longer needed. Compilers and assemblers may implement the following three-operand
pseudo-ops in addition to the four-operand VCMPPS instruction. See Table 3-5, where the notation of reg1 and reg2
represent either XMM registers or YMM registers. Compiler should treat reserved Imm8 values as illegal syntax.
Alternately, intrinsics can map the pseudo-ops to pre-defined constants to support a simpler intrinsic interface.
Compilers and assemblers may implement three-operand pseudo-ops for EVEX encoded VCMPPS instructions in a
similar fashion by extending the syntax listed in Table 3-5.
:
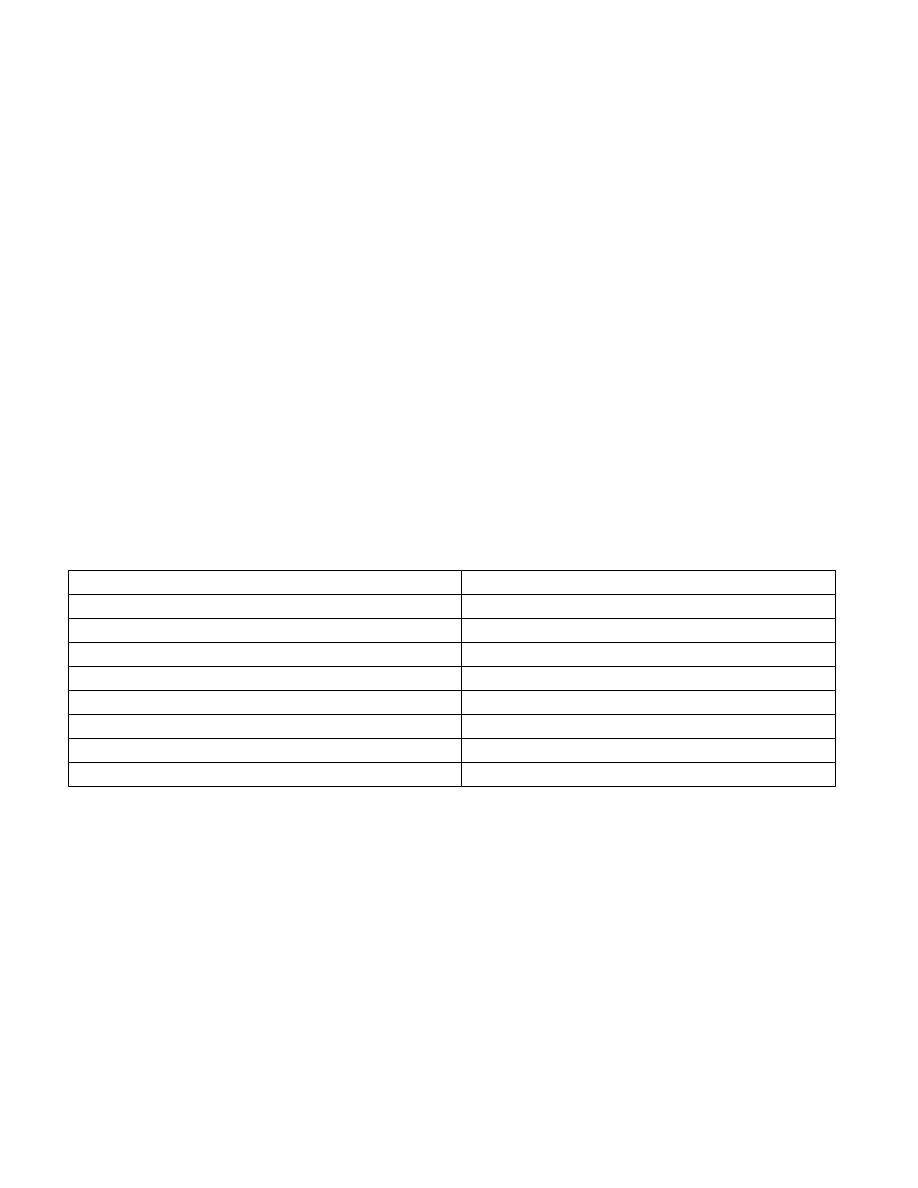
Table 3-4. Pseudo-Op and CMPPS Implementation
Pseudo-Op
CMPPS Implementation
CMPEQPS xmm1, xmm2
CMPPS xmm1, xmm2, 0
CMPLTPS xmm1, xmm2
CMPPS xmm1, xmm2, 1
CMPLEPS xmm1, xmm2
CMPPS xmm1, xmm2, 2
CMPUNORDPS xmm1, xmm2
CMPPS xmm1, xmm2, 3
CMPNEQPS xmm1, xmm2
CMPPS xmm1, xmm2, 4
CMPNLTPS xmm1, xmm2
CMPPS xmm1, xmm2, 5
CMPNLEPS xmm1, xmm2
CMPPS xmm1, xmm2, 6
CMPORDPS xmm1, xmm2
CMPPS xmm1, xmm2, 7