41-86 Vol. 3D
SGX INSTRUCTION REFERENCES
Operation
Temp Variables in EGETKEY Operational Flow
(* Make sure KEYREQUEST is properly aligned and inside the current enclave *)
IF ( (DS:RBX is not 128Byte aligned) or (DS:RBX is within CR_ELRANGE) )
THEN #GP(0); FI;
(* Make sure DS:RBX is an EPC address and the EPC page is valid *)
IF ( (DS:RBX does not resolve to an EPC address) or (EPCM(DS:RBX).VALID = 0) )
THEN #PF(DS:RBX); FI;
IF (EPCM(DS:RBX).BLOCKED = 1) )
THEN #PF(DS:RBX); FI;
(* Check page parameters for correctness *)
IF ( (EPCM(DS:RBX).PT ≠ PT_REG) or (EPCM(DS:RBX).ENCLAVESECS ≠ CR_ACTIVE_SECS) or (EPCM(DS:RBX).PENDING = 1) or
(EPCM(DS:RBX).MODIFIED = 1) or (EPCM(DS:RBX).ENCLAVEADDRESS ≠ (DS:RBX & ~0FFFH) ) or (EPCM(DS:RBX).R = 0) )
THEN #PF(DS:RBX);
FI;
(* Make sure OUTPUTDATA is properly aligned and inside the current enclave *)
IF ( (DS:RCX is not 16Byte aligned) or (DS:RCX is within CR_ELRANGE) )
THEN #GP(0); FI;
(* Make sure DS:RCX is an EPC address and the EPC page is valid *)
IF ( (DS:RCX does not resolve to an EPC address) or (EPCM(DS:RCX).VALID = 0) )
THEN #PF(DS:RCX); FI;
IF (EPCM(DS:RCX).BLOCKED = 1) )
THEN #PF(DS:RCX); FI;
(* Check page parameters for correctness *)
IF ( (EPCM(DS:RCX).PT ≠ PT_REG) or (EPCM(DS:RCX).ENCLAVESECS ≠ CR_ACTIVE_SECS) or (EPCM(DS:RCX).PENDING = 1) or
(EPCM(DS:RCX).MODIFIED = 1) or (EPCM(DS:RCX).ENCLAVEADDRESS ≠ (DS:RCX & ~0FFFH) ) or (EPCM(DS:RCX).W = 0) )
THEN #PF(DS:RCX);
FI;
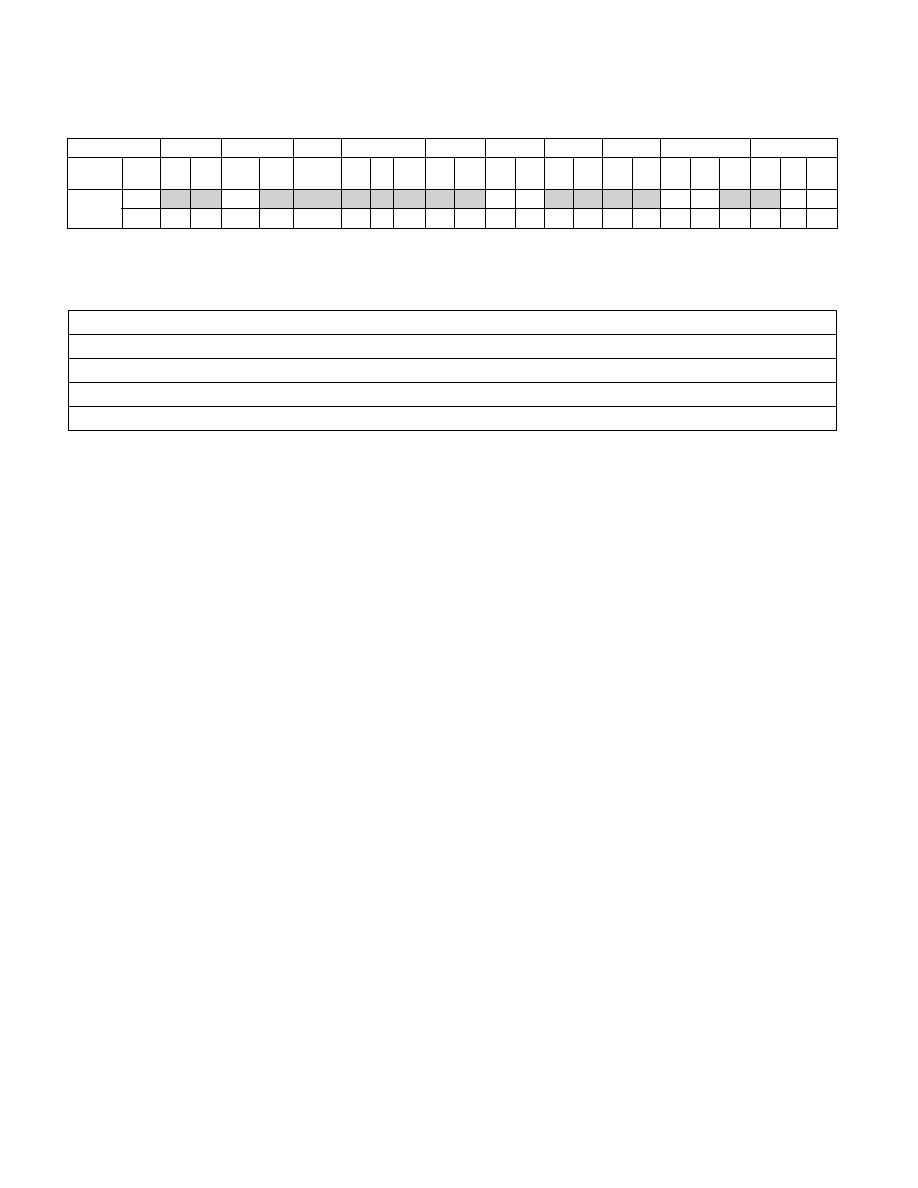
Table 41-59. Concurrency Restrictions of EGETKEY with Other Intel® SGX Operations 2 of 2
Operation
EREMOVE
EREPORT
ETRACK
EWB
EAUG
EMODPE
EMODPR
EMODT
EACCEPT
EACCEPTCOPY
Param Targ SECS Param SECS SECS
SRC VA SECS Targ SECS Targ SECI
NFO
Targ SEC
S
Targ SEC
S
Targ SECI
NFO
SECS Targ SR
C
SECI
NFO
EGETKEY
Param
U
Y
U
Y
U
Y
U
SECS
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Name
Type
Size (Bits)
Description
TMP_CURRENTSECS
Address of the SECS for the currently executing enclave.
TMP_KEYDEPENDENCIES
Temp space for key derivation.
TMP_ATTRIBUTES
128
Temp Space for the calculation of the sealable Attributes.
TMP_OUTPUTKEY
128
Temp Space for the calculation of the key.