Vol. 3D 38-15
ENCLAVE ACCESS CONTROL AND DATA STRUCTURES
38.15.1 REPORTDATA
REPORTDATA is a 64-Byte data structure that is provided by the enclave and included in the REPORT. It can be used
to securely pass information from the enclave to the target enclave.
38.16 REPORT TARGET INFO (TARGETINFO)
This structure is an input parameter to the EREPORT leaf function. The address of TARGETINFO is specified as an
effective address in RBX. It is used to identify the target enclave which will be able to cryptographically verify the
REPORT structure returned by EREPORT. TARGETINFO must be 512-Byte aligned.
38.17 KEY
REQUEST
(KEYREQUEST)
This structure is an input parameter to the EGETKEY leaf function. It is passed in as an effective address in RBX and
must be 512-Byte aligned. It is used for selecting the appropriate key and any additional parameters required in
the derivation of that key.
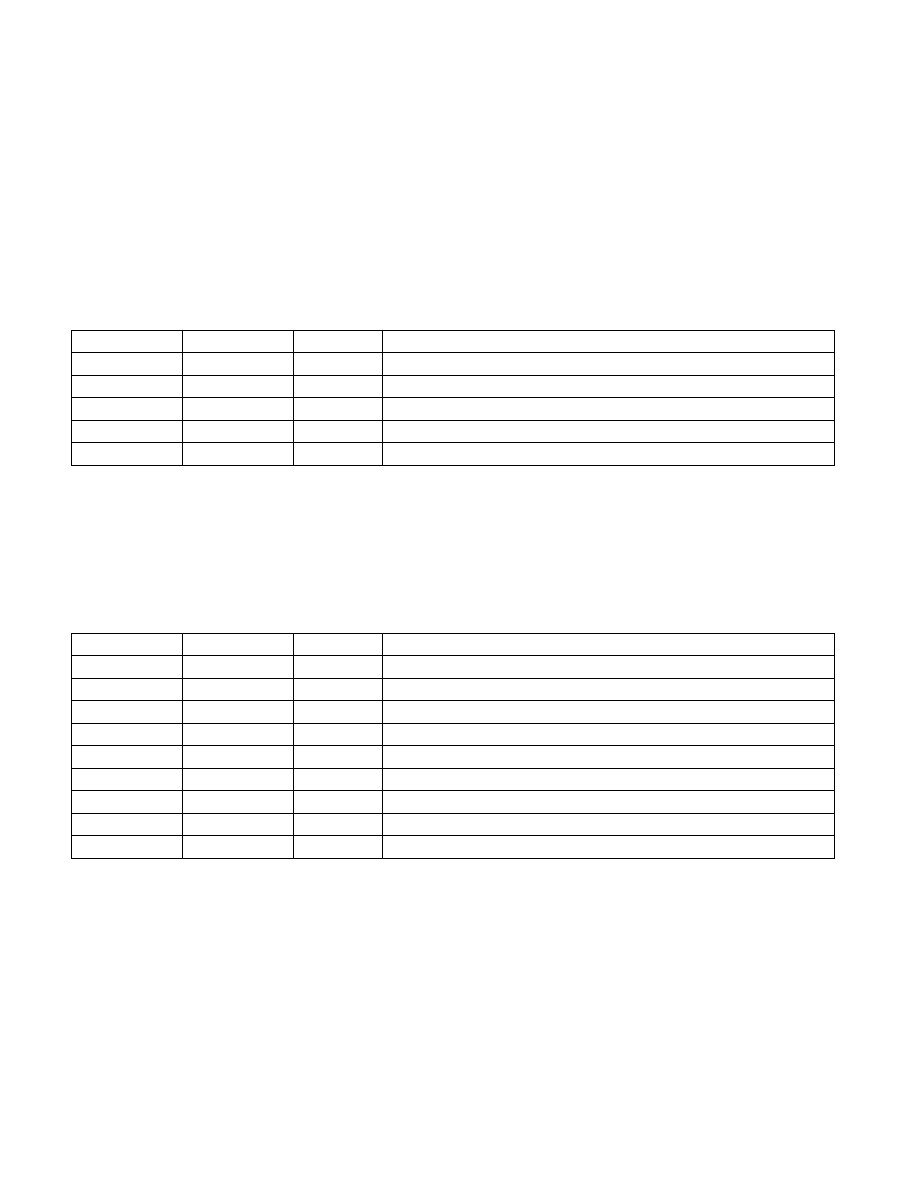
Table 38-22. Layout of TARGETINFO Data Structure
Field
OFFSET (Bytes) Size (Bytes)
Description
MEASUREMENT
0
32
The MRENCLAVE of the target enclave.
ATTRIBUTES
32
16
The ATTRIBUTES field of the target enclave.
RESERVED
48
4
MISCSELECT
52
4
The MISCSELECT of the target enclave.
RESERVED
56
456
Table 38-23. Layout of KEYREQUEST Data Structure
Field
OFFSET (Bytes) Size (Bytes)
Description
KEYNAME
0
02
Identifies the Key Required.
KEYPOLICY
02
02
Identifies which inputs are required to be used in the key derivation.
ISVSVN
04
02
The ISV security version number that will be used in the key derivation.
RESERVED
06
02
Must be zero.
CPUSVN
08
16
The security version number of the processor used in the key derivation.
ATTRIBUTEMASK 24
16
A mask defining which ATTRIBUTES bits will be included in key derivation.
KEYID
40
32
Value for key wear-out protection.
MISCMASK
72
4
A mask defining which MISCSELECT bits will be included in key derivation.
RESERVED
76
436