Vol. 3A 5-7
PROTECTION
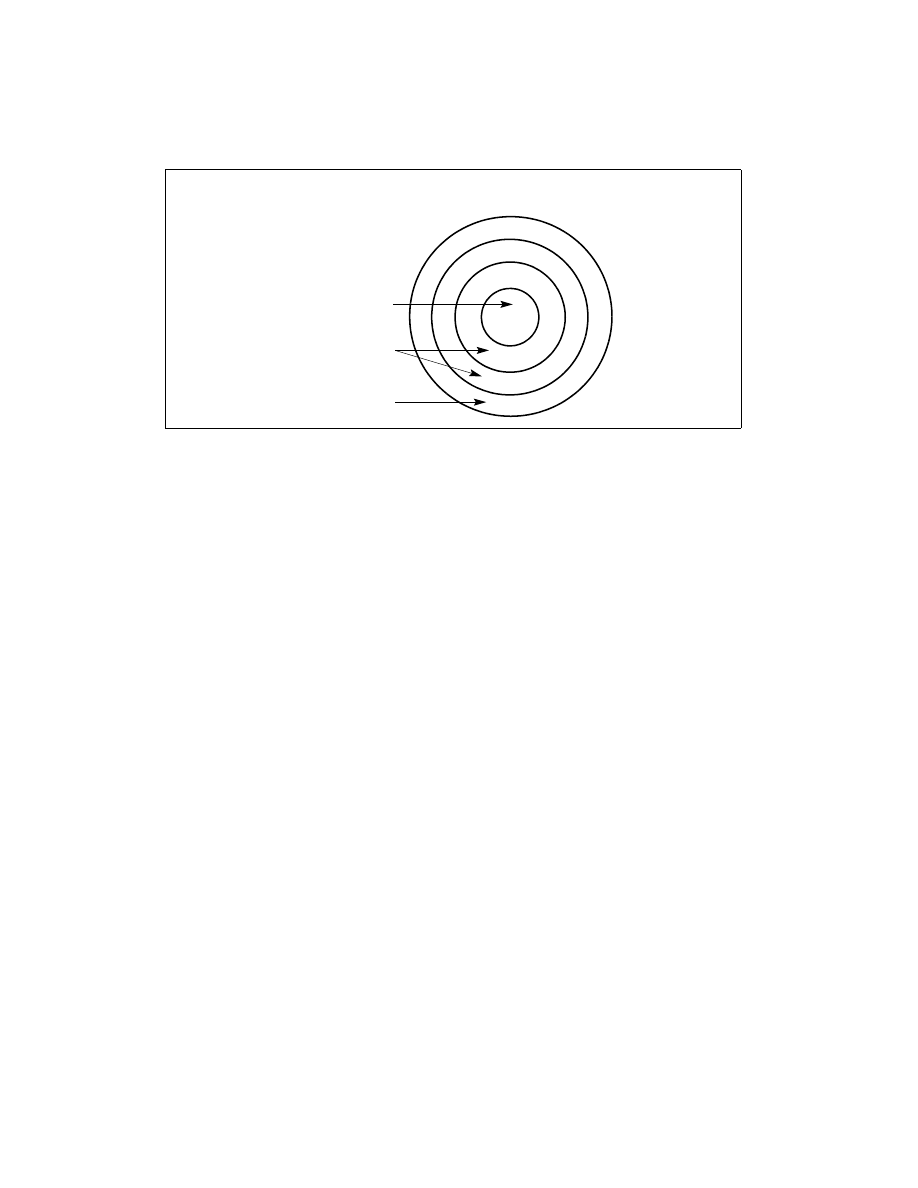
The center (reserved for the most privileged code, data, and stacks) is used for the segments containing the critical
software, usually the kernel of an operating system. Outer rings are used for less critical software. (Systems that
use only 2 of the 4 possible privilege levels should use levels 0 and 3.)
The processor uses privilege levels to prevent a program or task operating at a lesser privilege level from accessing
a segment with a greater privilege, except under controlled situations. When the processor detects a privilege level
violation, it generates a general-protection exception (#GP).
To carry out privilege-level checks between code segments and data segments, the processor recognizes the
following three types of privilege levels:
•
Current privilege level (CPL) — The CPL is the privilege level of the currently executing program or task. It
is stored in bits 0 and 1 of the CS and SS segment registers. Normally, the CPL is equal to the privilege level of
the code segment from which instructions are being fetched. The processor changes the CPL when program
control is transferred to a code segment with a different privilege level. The CPL is treated slightly differently
when accessing conforming code segments. Conforming code segments can be accessed from any privilege
level that is equal to or numerically greater (less privileged) than the DPL of the conforming code segment.
Also, the CPL is not changed when the processor accesses a conforming code segment that has a different
privilege level than the CPL.
•
Descriptor privilege level (DPL) — The DPL is the privilege level of a segment or gate. It is stored in the DPL
field of the segment or gate descriptor for the segment or gate. When the currently executing code segment
attempts to access a segment or gate, the DPL of the segment or gate is compared to the CPL and RPL of the
segment or gate selector (as described later in this section). The DPL is interpreted differently, depending on
the type of segment or gate being accessed:
— Data segment — The DPL indicates the numerically highest privilege level that a program or task can have
to be allowed to access the segment. For example, if the DPL of a data segment is 1, only programs running
at a CPL of 0 or 1 can access the segment.
— Nonconforming code segment (without using a call gate) — The DPL indicates the privilege level that
a program or task must be at to access the segment. For example, if the DPL of a nonconforming code
segment is 0, only programs running at a CPL of 0 can access the segment.
— Call gate — The DPL indicates the numerically highest privilege level that the currently executing program
or task can be at and still be able to access the call gate. (This is the same access rule as for a data
segment.)
— Conforming code segment and nonconforming code segment accessed through a call gate — The
DPL indicates the numerically lowest privilege level that a program or task can have to be allowed to access
the segment. For example, if the DPL of a conforming code segment is 2, programs running at a CPL of 0 or
1 cannot access the segment.
Figure 5-3. Protection Rings
Level 0
Level 1
Level 2
Level 3
Protection Rings
Operating
Operating System
Services
System
Kernel
Applications